What is Cryptocurrency?
Security Boulevard
SEPTEMBER 22, 2021
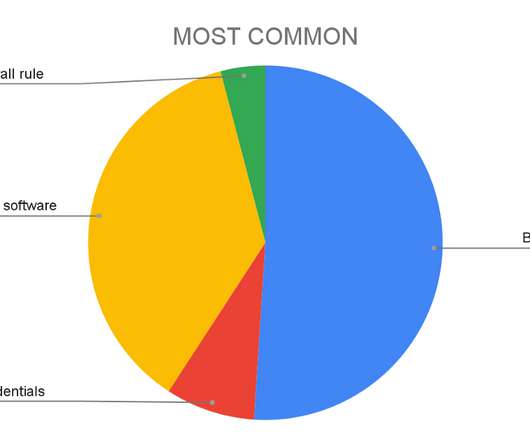
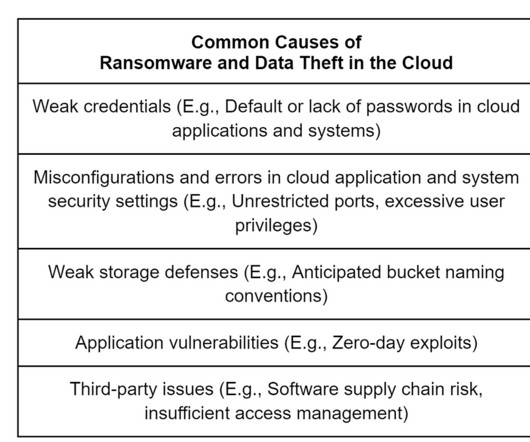
Cryptocurrency is best thought of as a digital currency that only exists on computers. Transaction data and the ledger are encrypted using cryptography. Cryptocurrency Main Features. Cryptocurrency Main Features. Let’s dig into how cryptocurrency works. Cryptocurrencies are decentralized and distributed.











































Let's personalize your content