Russian hackers exfiltrated data from Capita over a week before outage
DoublePulsar
APRIL 20, 2023
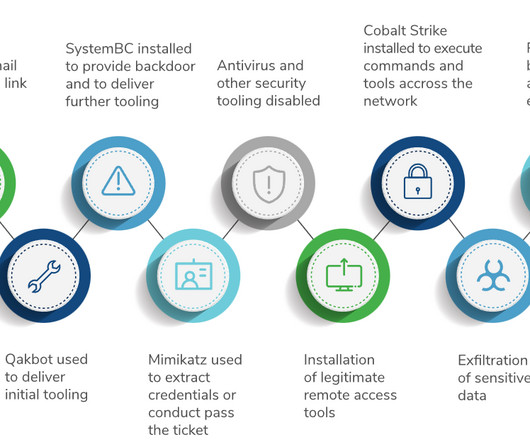
Russian hackers exfiltrated data from from Capita over a week before outage Capita have finally admitted a data breach , but still do not think they need to disclose key details of the incident to customers, regulators, impacted parties and investors. Why does this matter? Capita handle £6.5billion of UK government contracts.













Let's personalize your content