How Cobalt Strike Became a Favorite Tool of Hackers
eSecurity Planet
MARCH 14, 2022
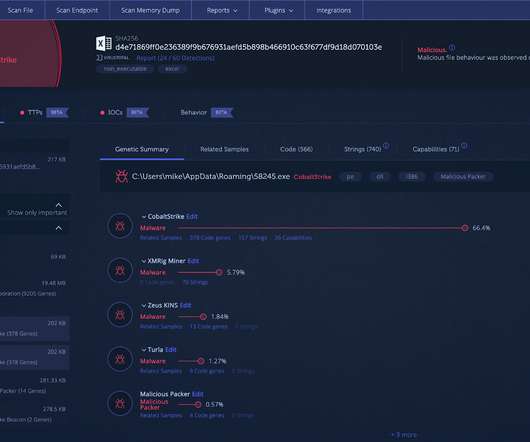
Cobalt Strike was created a decade ago by Raphael Mudge as a tool for security professionals. Indeed, the tool can assess vulnerabilities and run penetration tests , while most tools on the market cannot do both. Vulnerability assessment and pentesting are two different things. Cobalt Strike Attacks Make Headlines.





















Let's personalize your content