The Ups and Downs of 0-days: A Year in Review of 0-days Exploited In-the-Wild in 2022
Google Security
JULY 27, 2023
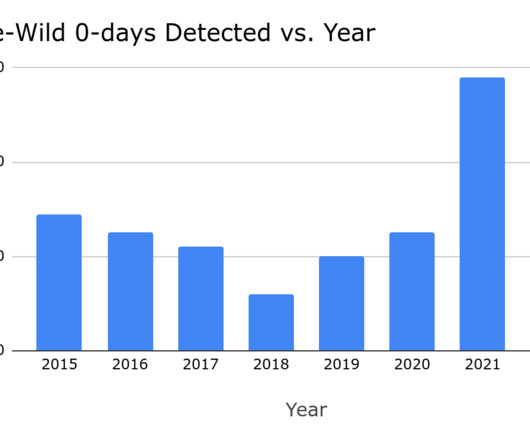
Maddie Stone, Security Researcher, Threat Analysis Group (TAG) This is Google’s fourth annual year-in-review of 0-days exploited in-the-wild [ 2021 , 2020 , 2019 ] and builds off of the mid-year 2022 review. Bug collisions are high. Project Zero wrote about one of these cases in November 2022 in their “Mind the Gap” blog post.









Let's personalize your content