How to Use Mayhem With Github Actions to Easily Secure Your Applications
ForAllSecure
MARCH 16, 2023
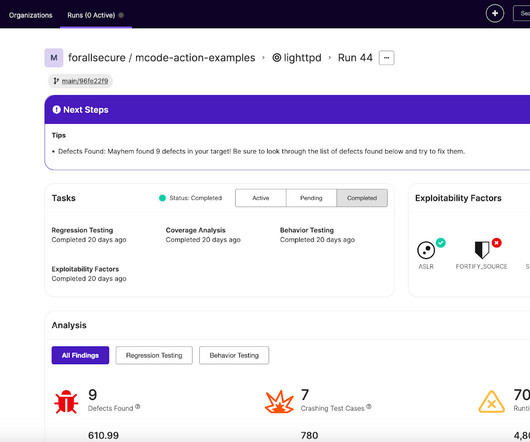
In this blog post, we’ll walk through the following: What is the Mayhem GitHub Action? That’s a lot of value from automating the traditional DevSecOps workflow! Once complete, you’ll need to modify any corresponding Mayhem.yml file to use your specific tagged release and test your changes.










Let's personalize your content