Hundreds of network operators’ credentials found circulating in Dark Web
Security Affairs
JANUARY 30, 2024
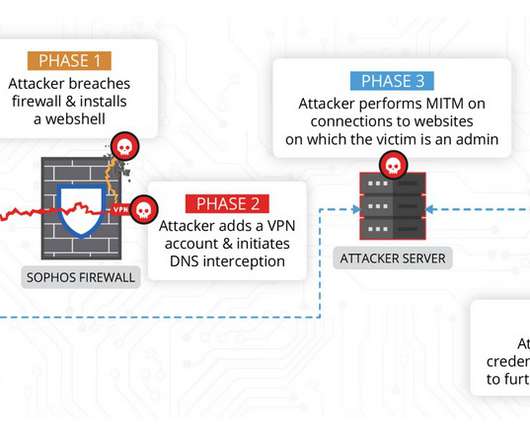
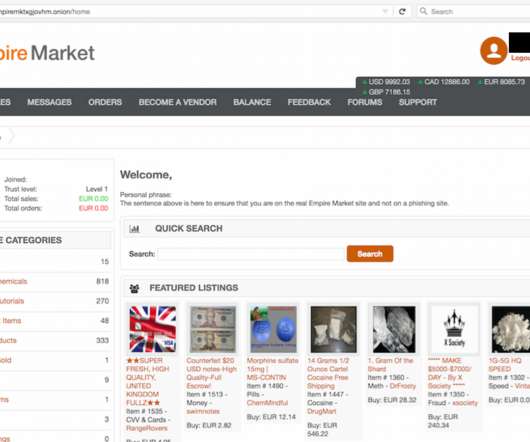
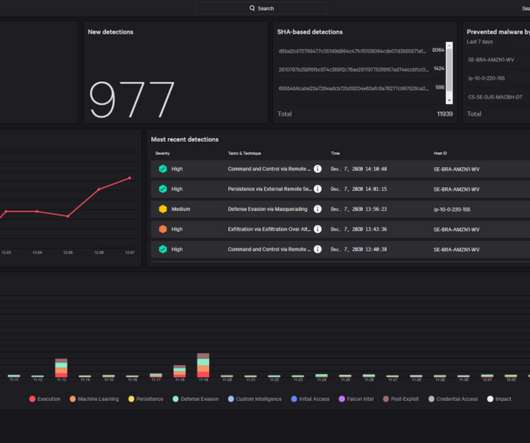
Following a recent and highly disruptive cyberattack on telecom carrier Orange España , the cybersecurity community needs to rethink its approach to safeguarding the digital identity of staff involved in network engineering and IT infrastructure management.
















































Let's personalize your content