Social engineering, deception becomes increasingly sophisticated
Security Affairs
FEBRUARY 20, 2023
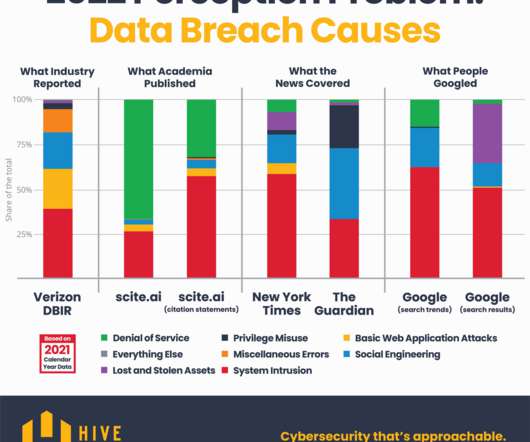
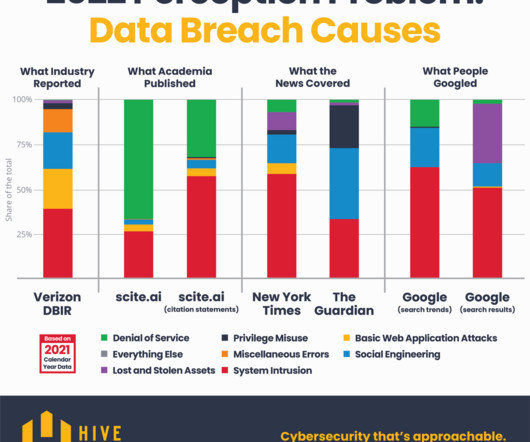
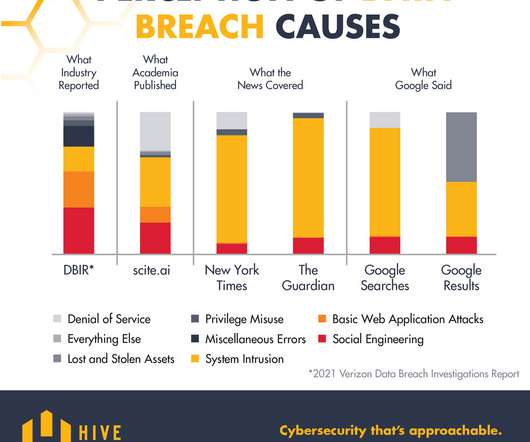
Social engineering techniques are becoming increasingly sophisticated and are exploiting multiple emerging means, such as deep fakes. The increasing use of videoconferencing platforms and the various forms of remote work also adopted in the post-emergency covid make interpersonal collaborations increasingly virtual.










































Let's personalize your content