JOKERSPY used to target a cryptocurrency exchange in Japan
Security Affairs
JUNE 27, 2023
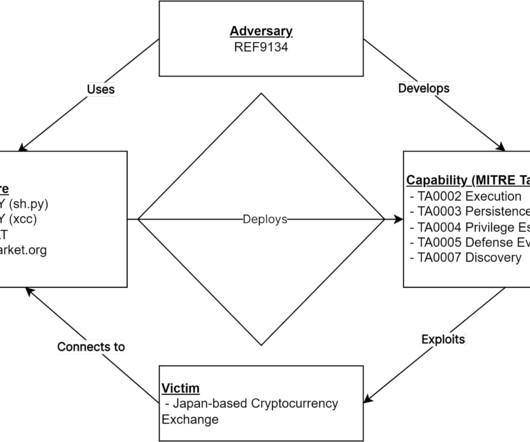
An unnamed Japanese cryptocurrency exchange was the victim of a cyber attack aimed at deploying an Apple macOS backdoor named JokerSpy. Elastic Security Labs researchers provided details about a recently discovered intrusion at an unnamed cryptocurrency exchange, aimed at deploying an Apple macOS backdoor named JokerSpy.












































Let's personalize your content