Threat actors exploit Ivanti VPN bugs to deploy KrustyLoader Malware
Security Affairs
JANUARY 31, 2024
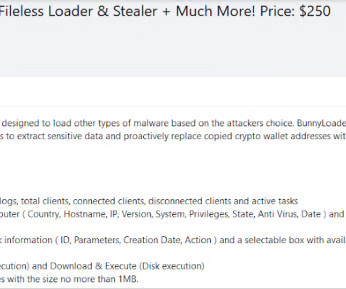
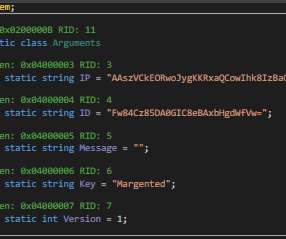
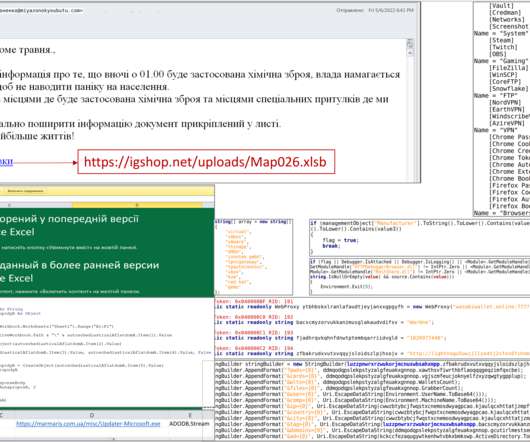
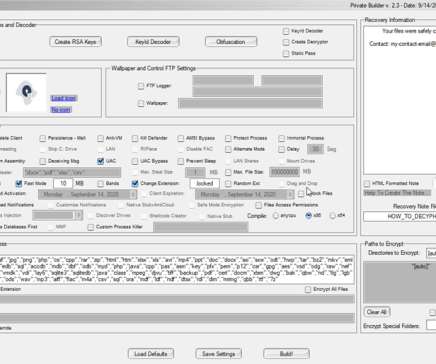
Threat actors are exploiting recently disclosed zero-day flaws in Ivanti Connect Secure (ICS) VPN devices to deliver KrustyLoader. Researchers from cybersecurity firm Synacktiv published a technical analysis of a Rust malware, named KrustyLoader, that was delivered by threat actors exploiting the above vulnerabilities.






































Let's personalize your content