OAuth apps used in cryptocurrency mining, phishing campaigns, and BEC attacks
Security Affairs
DECEMBER 13, 2023
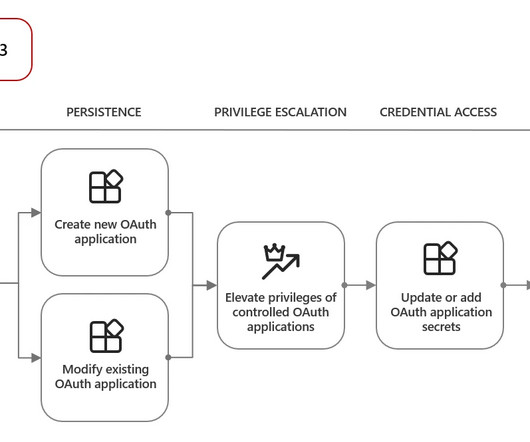
Microsoft warns that threat actors are using OAuth applications cryptocurrency mining campaigns and phishing attacks. Threat actors are using OAuth applications such as an automation tool in cryptocurrency mining campaigns and other financially motivated attacks. ” states Microsoft. ” continues the report.









































Let's personalize your content