How Cryptocurrency Turns to Cash in Russian Banks
Krebs on Security
DECEMBER 11, 2024
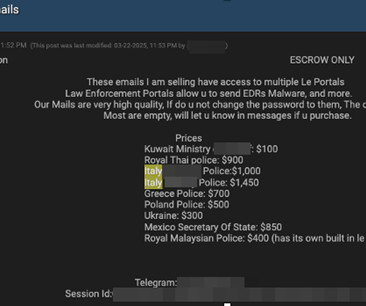
A financial firm registered in Canada has emerged as the payment processor for dozens of Russian cryptocurrency exchanges and websites hawking cybercrime services aimed at Russian-speaking customers, new research finds. A machine-translated version of Flymoney, one of dozens of cryptocurrency exchanges apparently nested at Cryptomus.

















































Let's personalize your content