Apple slaps hard against ‘mercenary’ surveillance-as-a-service industry
CSO Magazine
JULY 7, 2022
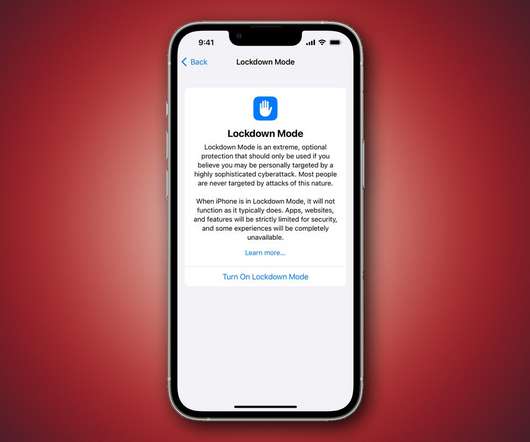
The company is introducing Lockdown Mode to protect high-risk individuals against corrosive surveillance and attacks, and investing millions to improve protection on its devices.






























Let's personalize your content