News alert: Beazley reports on how AI, new tech distract businesses as cyber risk intensifies
The Last Watchdog
JULY 13, 2023
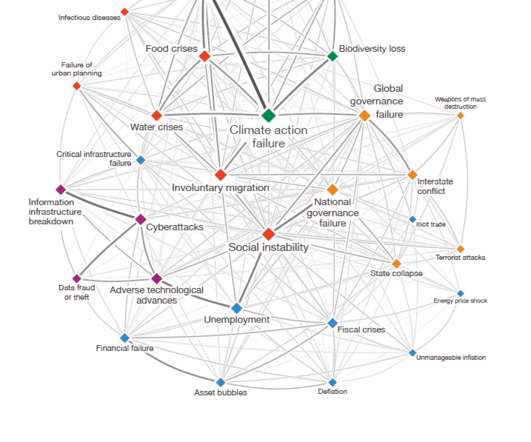
London, July 13, 2023 — Beazley, the leading specialist insurer, today published its latest Risk & Resilience report: Spotlight on: Cyber & Technology Risks 2023. Yet, boardroom focus on cyber risk appears to be diminishing. trillion by 2025, a 300% increase since 2015 1.

















































Let's personalize your content