Introduction to Fileless Malware
Doctor Chaos
DECEMBER 20, 2022
Fileless malware is a type of cyber attack that does not rely on the traditional method of installing malicious software on a victim's computer.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Doctor Chaos
DECEMBER 20, 2022
Fileless malware is a type of cyber attack that does not rely on the traditional method of installing malicious software on a victim's computer.

Adam Levin
OCTOBER 8, 2019
In a Private Industry Notification (PIN), the FBI warned businesses that “cyber actors” had been observed, “circumventing multi-factor authentication through common social engineering and technical attacks.” The methods used were SIM swapping , phishing , and newer hacking tools such as Muraena and Necrobrowser.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Mitnick Security
APRIL 5, 2021
Social engineering attacks account for a massive portion of all cyber attacks, and studies show that these attacks are on the rise. According to KnowBe4 , more than 90% of successful hacks and data breaches start with a common type of social engineering attack called phishing.

Hacker's King
DECEMBER 16, 2024
In the digital age, cyber-attacks are a growing concern for individuals, businesses, and governments worldwide. These attacks are becoming more sophisticated, targeted, and damaging, threatening data privacy, financial stability, and national security.

SecureWorld News
NOVEMBER 8, 2023
Social engineering attacks have long been a threat to businesses worldwide, statistically comprising roughly 98% of cyberattacks worldwide. The average business faces more than 700 of these types of attacks every single year.

Jane Frankland
MAY 3, 2025
Allegedly orchestrated by the same group known as Scattered Spider, these attacks highlight the significant challenges even the most respected and established brands face in defending against modern cyber threats. Then, the focus of cyber attacks on retailers, and what lessons must be learned by business leaders and customers.

Digital Shadows
JANUARY 22, 2025
In this blog, well preview the reports highlights and give insights into social engineering campaigns leveraging impersonating domains and our predictions for the threats shaping 2025. Use early detection tools like honeypots or CanaryTokens to counter attackers using tools like Nmap and Angry IP Scanner.

SecureWorld News
MARCH 17, 2025
You must equip your staff with the knowledge to recognize phishing attempts, social engineering ploys, and other common cyber threats through regular, targeted training sessions. You also need a clear and well-practiced incident response plan in place.

Security Boulevard
NOVEMBER 14, 2022
A cybercriminal superstoreThe dark web, which can be accessed using special browsers like Tor, is a treasure trove of information, data, and software for carrying out cyber attacks.Reddit for CybercrimeThe Internet connects people. In the case of the dark web, this can be negative as cyber attackers find like-minded and motivated people.

Hacker's King
MAY 24, 2025
While these octopi of terror could spring from many sources, do you know what the very wellspring of most cyber attacks is? The startling fact is that more than 55% of breaches stem from credential attack vectors. Credential-based attacks include usernames, passwords, and tokens.

Security Affairs
FEBRUARY 20, 2023
Social engineering techniques are becoming increasingly sophisticated and are exploiting multiple emerging means, such as deep fakes. The human factor must always be considered as the first bastion of defense, even and especially against the most sophisticated cyber attacks. Deepfake technology, what’s it?

CyberSecurity Insiders
MARCH 23, 2021
To all those who are concerned about the increase in cyber attacks on Maritime Industry, here’s an interesting finding to analyze. During a webinar conducted by Riviera, they revealed that the Human errors are causing an increase in cyber attacks on Maritime Industry.

CyberSecurity Insiders
JANUARY 17, 2022
North Korea, the nation that is being led by Kim Jong UN is back into news headlines for stealing cryptocurrency worth millions through cyber attacks. The post North Korea steals $400m cryptocurrency through Cyber Attacks appeared first on Cybersecurity Insiders.

Tech Republic Security
JUNE 4, 2024
Organisations providing services related to the Paris Olympics 2024 have an increased risk of cyber attack, a new study has found.

CyberSecurity Insiders
MAY 11, 2023
Tokyo MoU, the most active regional port control organization in the Asia Pacific, has revealed that its data was compromised for months and that hackers gained fraudulent access through a cyber attack. It is unclear how the attack has impacted the servers of the Port State Control (PSC) platform.

CyberSecurity Insiders
FEBRUARY 17, 2023
Succession Wealth, a financial wealth management service offering company, has released a press statement that a cyber attack targeted its servers and it can only reveal details after the investigation gets concluded. Prima Facie revealed that hackers accessed no client data in the attack.

Digital Shadows
NOVEMBER 26, 2024
Key Points Phishing incidents rose during the reporting period (August 1 to October 31, 2024), accounting for 46% of all customer incidents. This increase is likely driven by high employee turnover and easy access to phishing kits. Meanwhile, “RansomHub” is rising rapidly due to its attractive ransomware-as-a-service (RaaS) model.
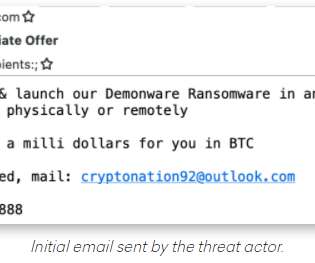
Krebs on Security
AUGUST 19, 2021
“According to this actor, he had originally intended to send his targets—all senior-level executives—phishing emails to compromise their accounts, but after that was unsuccessful, he pivoted to this ransomware pretext,” Hassold wrote.

Penetration Testing
MAY 2, 2025
A new threat intelligence report from EclecticIQ unveils the evolving tradecraft of Luna Moth, a financially motivated threat The post Luna Moth’s Callback Phishing Attacks Target US Legal and Financial Firms appeared first on Daily CyberSecurity.

Approachable Cyber Threats
MARCH 12, 2025
Category Awareness, Social Enginering Risk Level Phishing emails are getting harder to detect. What is phishing, and why is it such a big deal?" Phishing is one of the oldest tricks in the hacker playbook - but its also one of the most effective. Alright, but cant I just spot and delete phishing emails?"

CyberSecurity Insiders
APRIL 4, 2023
Social engineering – specifically malicious cyber campaigns delivered via email – remain the primary source of an organization’s vulnerability to attack. Popularised in the 1990s, email security has challenged cyber defenders for almost three decades. billion phishing e-mails get delivered every day.

IT Security Guru
NOVEMBER 1, 2024
Cybersecurity Threats and Digital Warfare One of the most significant threats to national security in the modern era is cyber warfare. Cyber attacks can compromise critical infrastructure, financial systems, and sensitive government data.
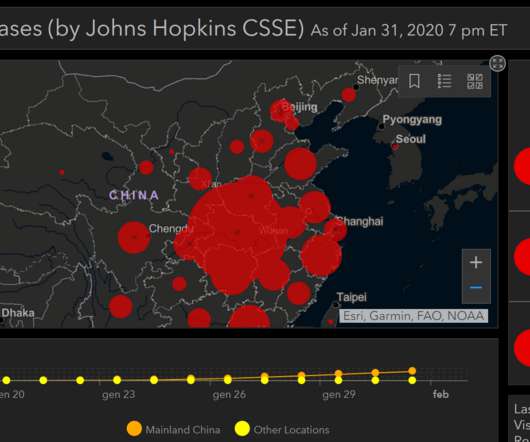
Security Affairs
FEBRUARY 26, 2020
Nowadays, it is common to say that the physical world and the cyber world are strictly connected. The proof is the leverage of the current physical threat, the CoronaVirus (COVID-19), as a social engineering trick to infect the cyber world. New Cyber Attack Campaign Leverages the COVID-19 Infodemic.

Security Affairs
MAY 13, 2025
The DragonForce group claimed the attack on M&S and Co-op, and told the BBC that they have attempted to hack Harrods. BleepingComputer reported that DragonForce ransomware affiliates usedScattered Spider social engineering tacticsto target Marks and Spencer.

CyberSecurity Insiders
JANUARY 25, 2023
United States Cybersecurity and Infrastructure Security Agency (CISA) along with two other agencies; National Security Agency (NSA) and Multi-State Information Sharing and Analysis Center (MS-ISAC) have issued a warning to federal agencies against a phishing scam taking place through Remote Monitoring and Management (RMM) Software.

Hot for Security
MARCH 18, 2021
The Cybersecurity & Infrastructure Security Agency (CISA) and the FBI have released a Joint Cybersecurity Advisory on TrickBot warning that a sophisticated group of cyber actors are sending phishing emails claiming to contain proof of traffic violations to lure victims into downloading the insidious malware.

The Last Watchdog
APRIL 28, 2020
As coronavirus-themed cyber attacks ramp up, consumers and companies must practice digital distancing to keep themselves protected. That, of course, presents the perfect environment for cybercrime that pivots off social engineering. Sadly, coronavirus phishing and ransomware hacks already are in high gear.

CyberSecurity Insiders
JANUARY 7, 2022
user accounts related to 17 companies was reportedly compromised in a Credential Stuffing Cyber Attack. To those unaware of such attacks, here’s a gist. A credential stuffing is a kind of automated online process where hackers attempt to access online accounts by using usernames and passwords sourced from various cyber attacks.

The Last Watchdog
NOVEMBER 27, 2018
The vast majority of cyber attacks against organizations pivot off the weakest security link: employees. The good news is that companies today have ready access to a wide variety of tools that can simulate common types of attacks and boost employee awareness. This service offers automated phishing tests and training modules.

The Last Watchdog
JUNE 1, 2021
It is an online scam attack quite similar to Phishing. The term Pharming is a combination of two words Phishing and Farming. It is a type of social engineering cyberattack in which the website’s traffic is manipulated to steal confidential credentials from the users. Pharming vs phishing.

Security Affairs
FEBRUARY 8, 2024
26 key cyber security stats for 2024 that every user should know, from rising cyber crime rates to the impact of AI technolog y. Cyber Crime Surge: During COVID-19 , cyber crimes shot up by 600%, showing how threats adapt to global changes. Phishing Attacks: Phishing is the top cyber attack, causing 90% of data breaches.

Security Boulevard
AUGUST 21, 2024
Attacks today can be executed through a myriad of communication channels, including emails, social media and mobile applications. The post The Golden Age of Impersonation: The Dual Role of AI in Cyber Attacks & Cyber Defense appeared first on Security Boulevard.

Security Boulevard
MARCH 17, 2025
In reality, many of the most successful breaches stem from simple tactics like phishing emails, social engineering, and exploiting basic security misconfigurations. People frequently fall for scams, phishing, and other attacks due to a lack of awareness, trust in seemingly legitimate sources, or simple human error.

Security Affairs
OCTOBER 18, 2018
Group-IB has estimated that crypto exchanges suffered a total loss of $882 million due to targeted attacks between 2017 and 2018. In most cases, cybercriminals, while attacking cryptocurrency exchanges, use traditional tools and methods, such as spear phishing, social engineering, distribution of malware, and website defacement.

The Last Watchdog
AUGUST 18, 2021
There are simple steps consumers can take today, for free, to lower their overall risk of a cyber attack, including using multi-factor authentication for their accounts and using strong passwords. Also, one of the top ways attackers can target individuals is via social engineering or phishing.

The Last Watchdog
JULY 24, 2023
Today, bad actors are ruthlessly skilled at cracking passwords – whether through phishing attacks, social engineering, brute force, or buying them on the dark web. In fact, according to Verizon’s most recent data breach report, approximately 80 percent of all breaches are caused by phishing and stolen credentials.

SecureWorld News
DECEMBER 30, 2024
Web application vulnerabilities To prevent attackers from interfering with the operation of web applications, experts recommend using a Web Application Firewall (WAF). It serves as a barrier between web applications and the Internet, identifying traces of various cyber attacks.

Security Affairs
OCTOBER 10, 2018
Security firm Group-IB has estimated that in H2 2017-H1 2018 cyber attacks caused $49.4 Group-IB, an international company that specializes in preventing cyber attacks, has estimated that in H2 2017-H1 2018 cyber attacks caused $49.4 Using web phishing, criminals have managed to steal $3.7 million (2.96

SecureWorld News
JUNE 17, 2024
Ezra Graziano, Director of Federal Accounts at Zimperium, emphasized the urgency for defense against such evolving social engineering tactics. While the exact perpetrators are unclear, he suggested nation-state actors or "phishing-as-a-service" groups could be involved.

Approachable Cyber Threats
MARCH 22, 2021
Through phishing. What’s phishing again?” Phishing is a specific type of cyber attack through which hackers and scammers use email to trick you. It’s part of a broader cyber attack called “social engineering” that includes other avenues like phone calls, text messages, and even impersonating people in real life.

Tech Republic Security
JANUARY 24, 2024
See the National Cyber Security Centre's predictions for generative AI for cyber attack and defense through 2025.
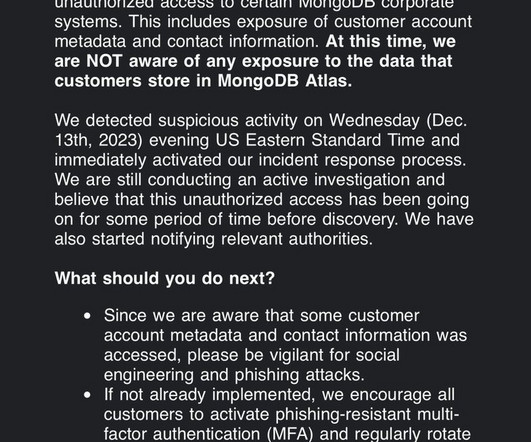
Security Affairs
DECEMBER 17, 2023
MongoDB on Saturday disclosed it is investigating a cyber attack against certain corporate systems. The cyber attack was discovered on December 13, 2023, and led to the exposure of customer account metadata and contact information. .”

Duo's Security Blog
FEBRUARY 27, 2024
In this part, we’ll evaluate each method’s effectiveness in defending against five common types of cyber-attack. Threat type #3: Phishing and MFA fatigue Phishing attacks and MFA fatigue attacks are related threats in which a user is given a fraudulent prompt to authenticate.

Identity IQ
JUNE 1, 2023
The Rise of AI Social Engineering Scams IdentityIQ In today’s digital age, social engineering scams have become an increasingly prevalent threat. Social engineering scams leverage psychological manipulation to deceive individuals and exploit the victims’ trust. Phishing attacks.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content