NEW TECH: Trend Micro flattens cyber risks — from software development to deployment
The Last Watchdog
AUGUST 25, 2020
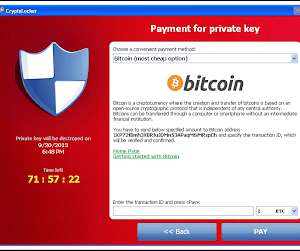
MSSPs started out some 15 years ago providing email security and firewall upkeep, but today they often provide vulnerability patching and even endpoint detection and response ( EDR ) services, as well. Ransomware purveyors seek out open RDP ports , which have become the prime path for them to spread their cyber extortion campaigns.

















































Let's personalize your content