GUEST ESSAY: Leveraging DevSecOps to quell cyber risks in a teeming threat landscape
The Last Watchdog
JANUARY 2, 2024
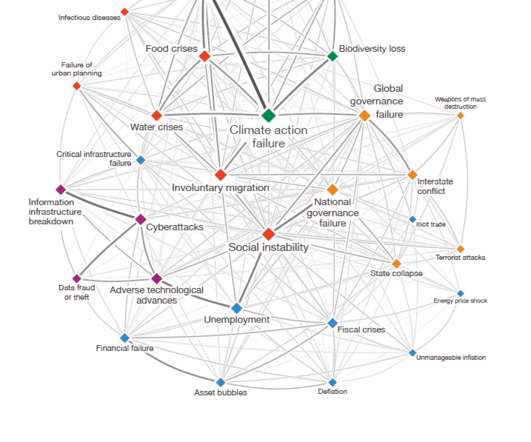
In today’s digital landscape, organizations face numerous challenges when it comes to mitigating cyber risks. Related: How AI is transforming DevOps The constant evolution of technology, increased connectivity, and sophisticated cyber threats pose significant challenges to organizations of all sizes and industries.


















































Let's personalize your content