6 Business functions that will benefit from cybersecurity automation
CyberSecurity Insiders
OCTOBER 28, 2021
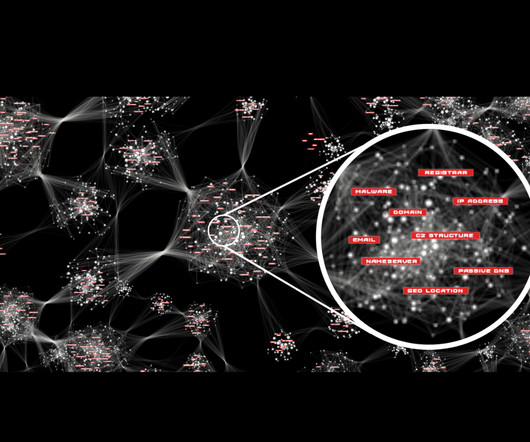
Enterprises and small businesses alike are facing challenges that impact their ability to maintain adequate cybersecurity. Cybersecurity automation trained with machine learning and powered by AI is helping to close vulnerability gaps and lower the cost of cybersecurity incidents. The business case for automation.





















Let's personalize your content