Sipping from the Coronavirus Domain Firehose
Krebs on Security
APRIL 16, 2020
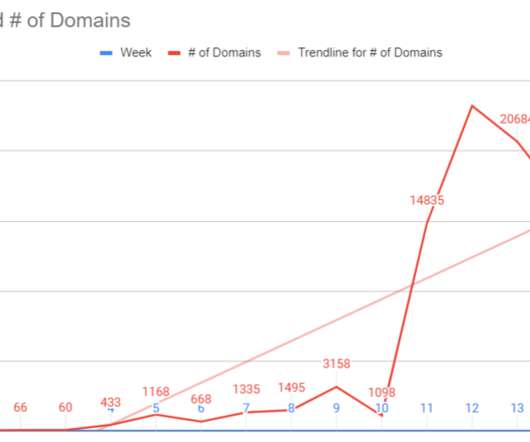
Data from security vendor Sophos, published by the Cyber Threat Coalition, shows the number of Coronavirus or COVID-19 themed domains registered per week that received traffic. “Looking at the data collected, the pattern of visits are highest on Monday and Friday, and the lowest visit count is on the weekend. .
























Let's personalize your content