DRM Report Q2 2023 – Ransomware threat landscape
Security Affairs
OCTOBER 4, 2023
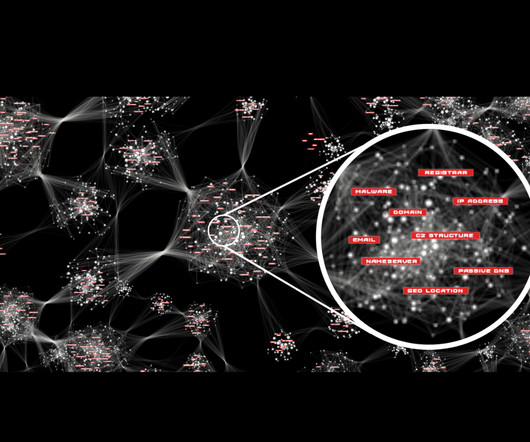
The DRM Report Q2 2023 report provides a detailed insight into the ransomware threat landscape during the period between May and August 2023. In an era where digitalization has woven its web into the very fabric of our lives, the dark underbelly of the digital realm continues to pose an ever-growing threat.
























Let's personalize your content