Europol lifts the lid on cybercrime tactics
Malwarebytes
SEPTEMBER 15, 2023
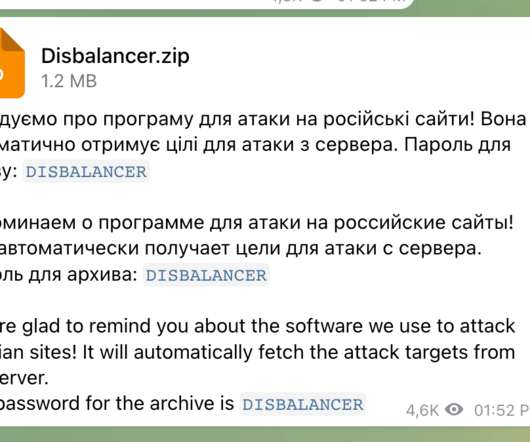
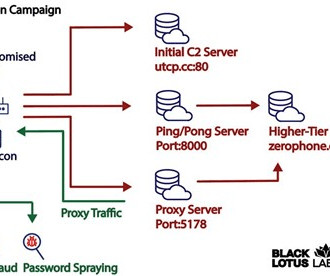
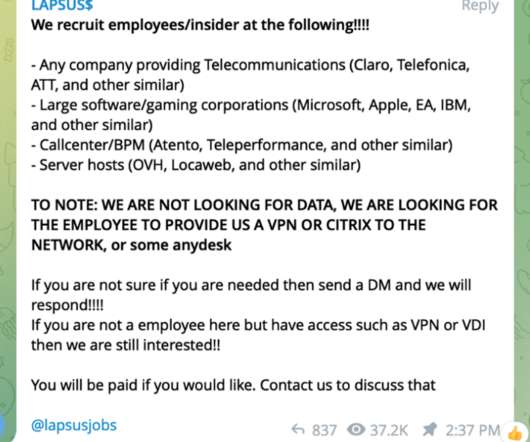
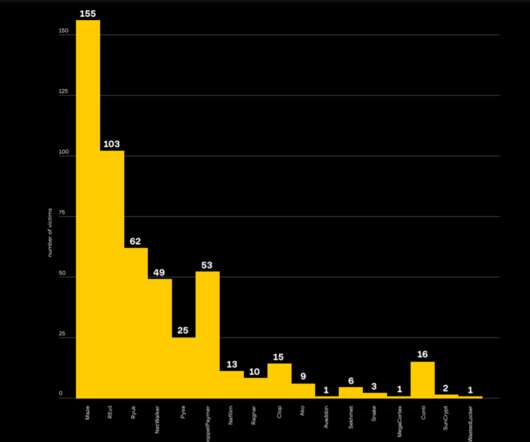
The report follows the Internet Organized Crime Assessment (IOCTA), Europol’s assessment of the cybercrime landscape and how it has changed over the last 24 months. The information theft is also seen to be feeding an ecosystem of criminals dealing in and making use of personal and financial information.














































Let's personalize your content