Malvertising Is a Cybercrime Heavyweight, Not an Underdog
SecureWorld News
MARCH 29, 2024
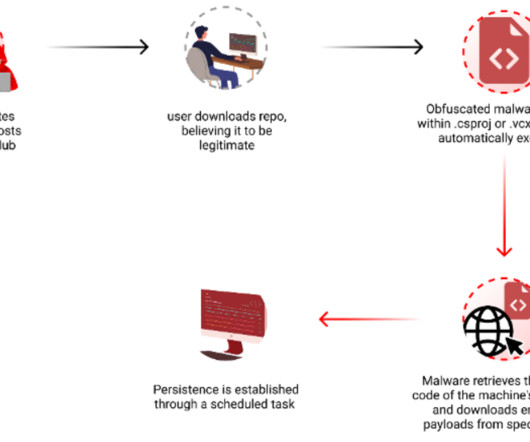
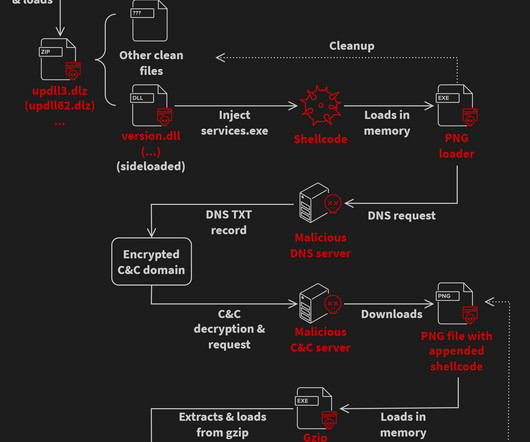
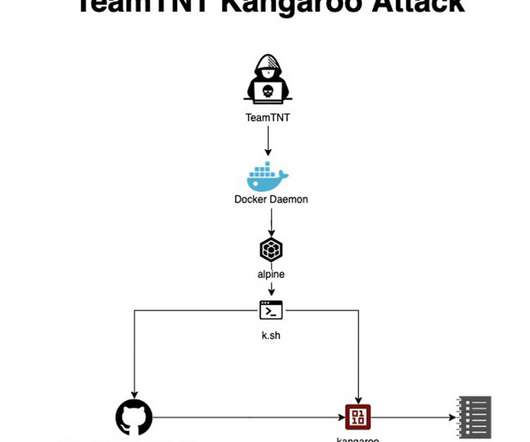
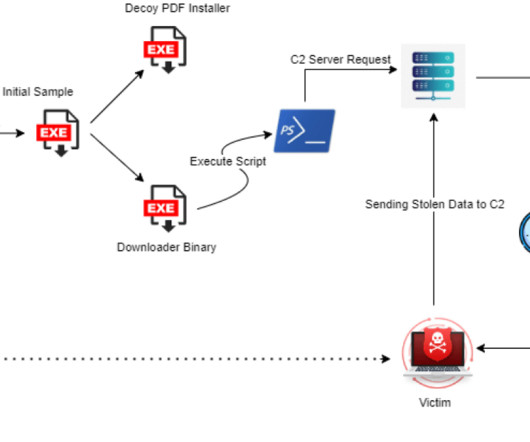
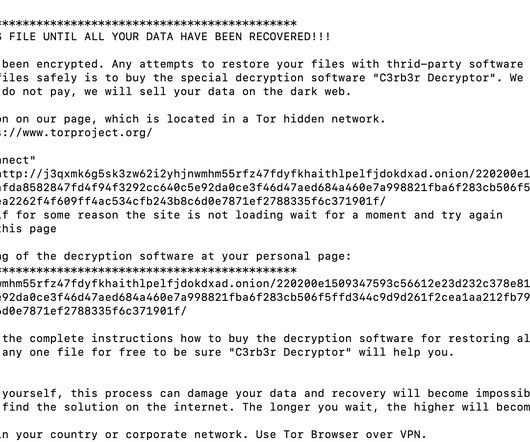
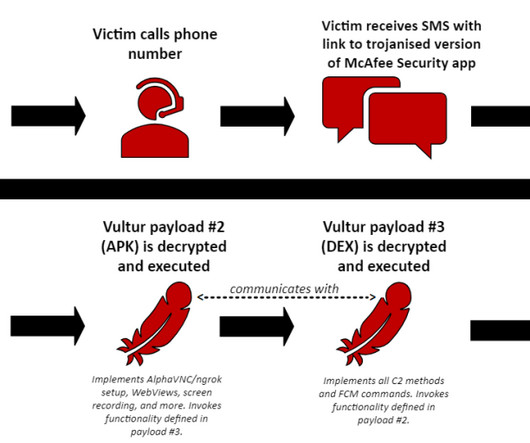
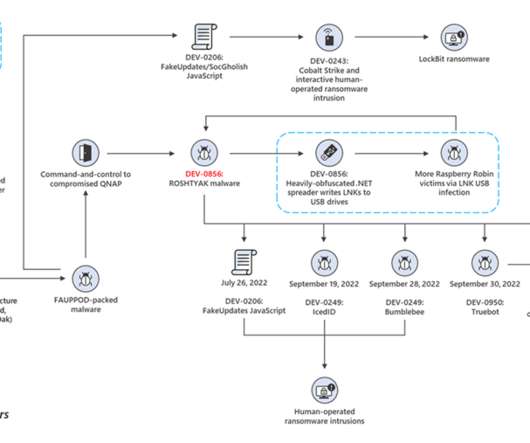
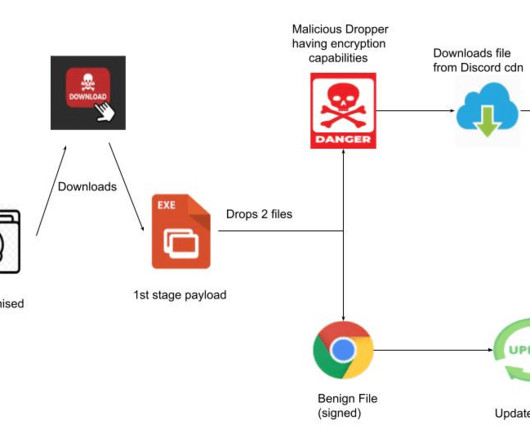
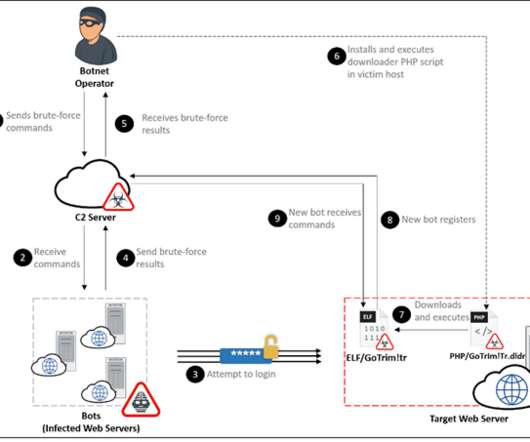
Malvertising acts as a vessel for malware propagation. To set such a stratagem in motion, cybercriminals poison legitimate websites with ads that lead to shady URLs or download malicious code camouflaged as something harmless. A stepping stone to impactful cybercrime This tactic has tangible real-world implications.




























Let's personalize your content