Crooks manipulate GitHub’s search results to distribute malware
Security Affairs
APRIL 13, 2024
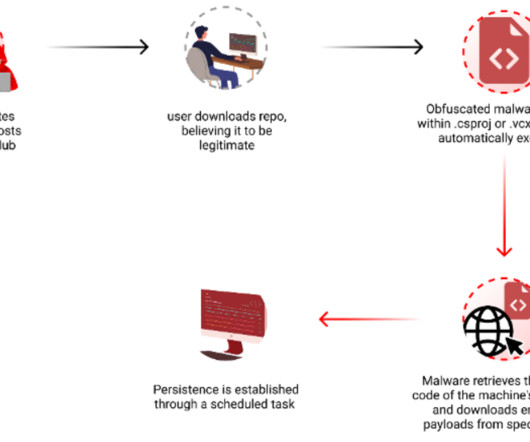
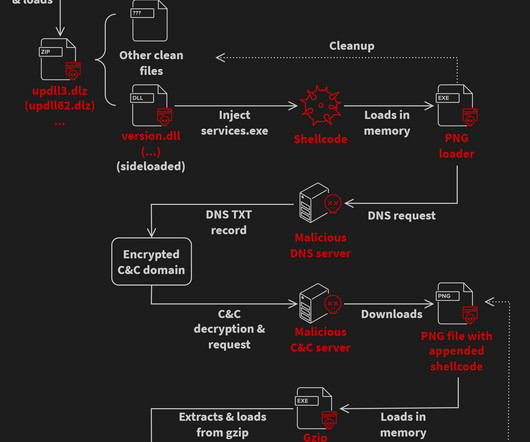
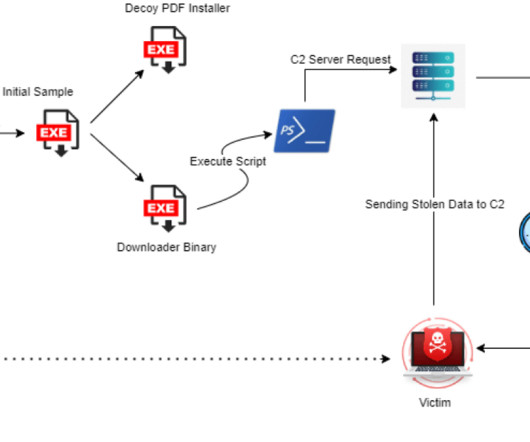
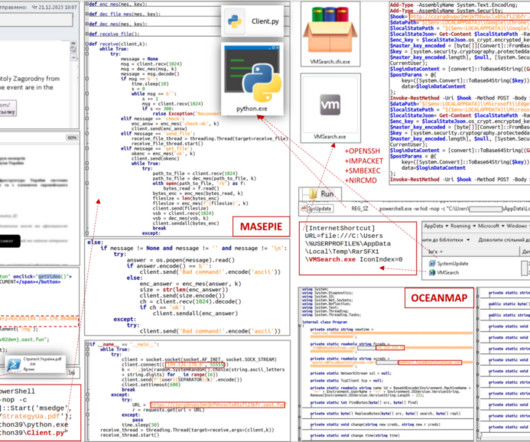
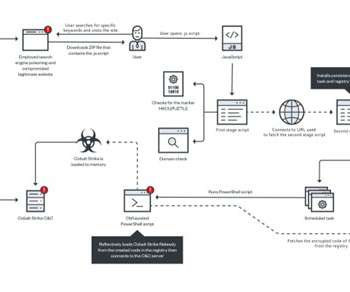
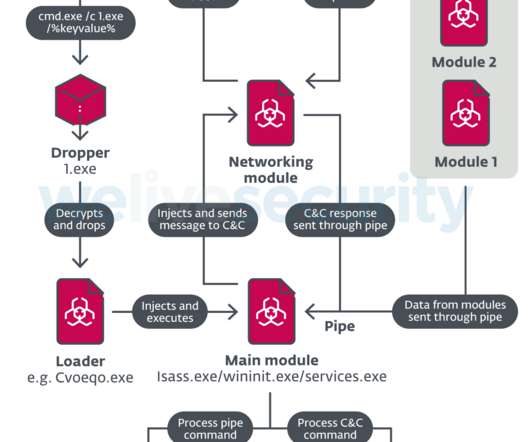
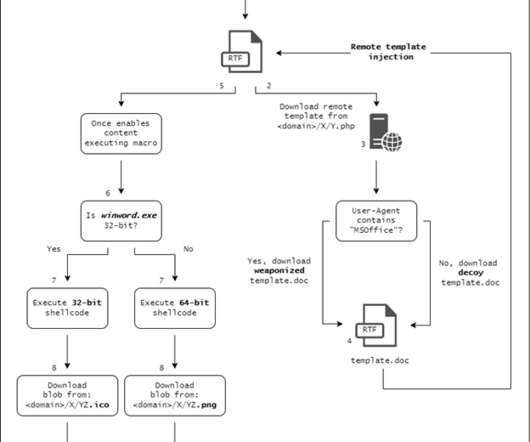
Researchers warn threat actors are manipulating GitHub search results to target developers with persistent malware. Checkmarx researchers reported that t hreat actors are manipulating GitHub search results to deliver persistent malware to developers systems. The archive contained an executable named feedbackAPI.exe.




































Let's personalize your content