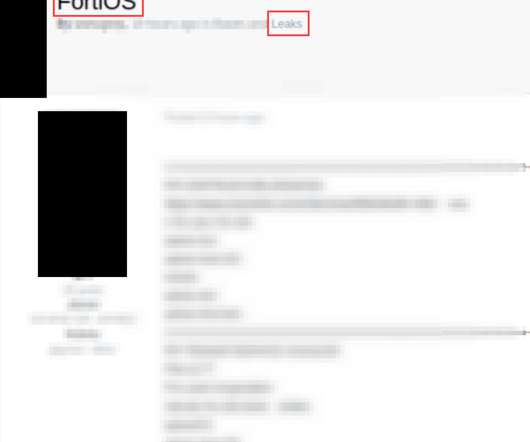
Threat actors are offering access to corporate networks via unauthorized Fortinet VPN access
Security Affairs
NOVEMBER 29, 2022
In early October, Fortinet addressed the critical authentication bypass flaw, tracked as CVE-2022-40684, that impacted FortiGate firewalls and FortiProxy web proxies. The company urged customers to address this critical vulnerability immediately due to the risk of remote exploitation of the flaw. and from 7.2.0 and 7.2.0.























Let's personalize your content