TeamTNT cybercrime gang expands its arsenal to target thousands of orgs worldwide
Security Affairs
SEPTEMBER 9, 2021
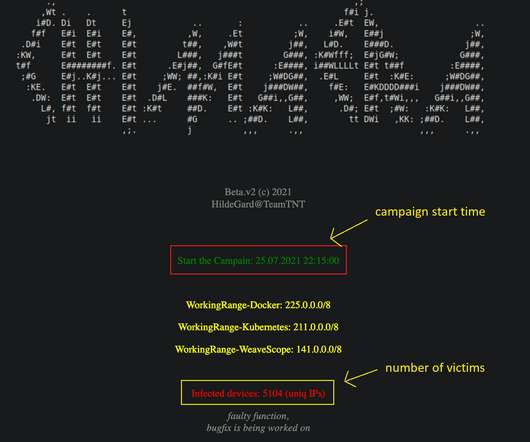
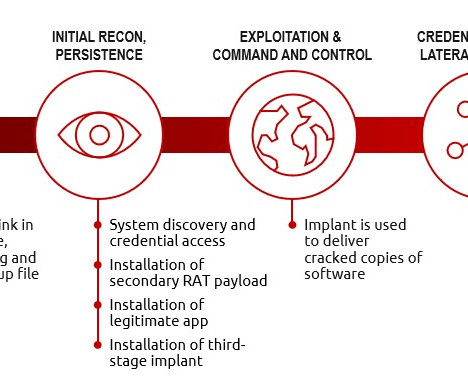
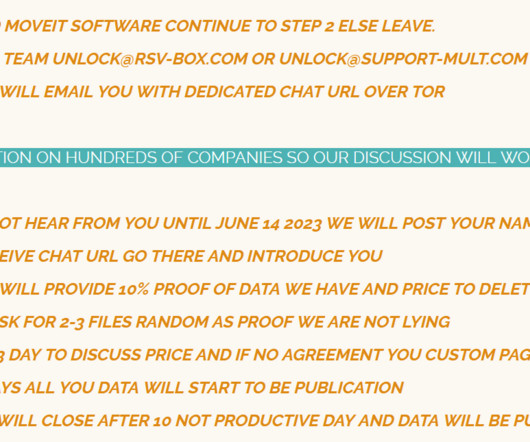
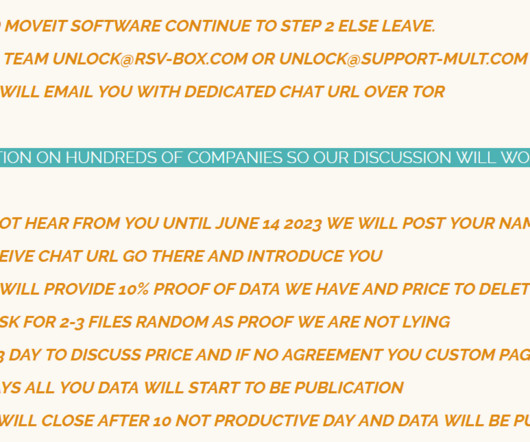
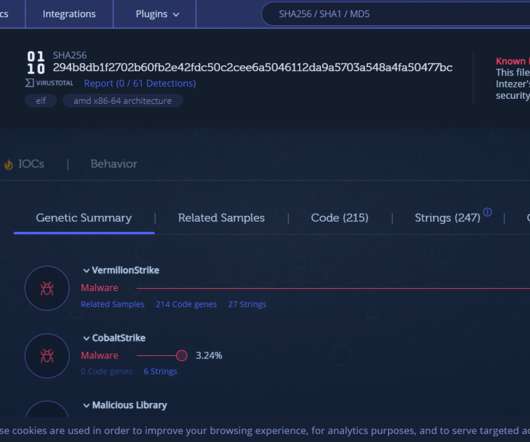
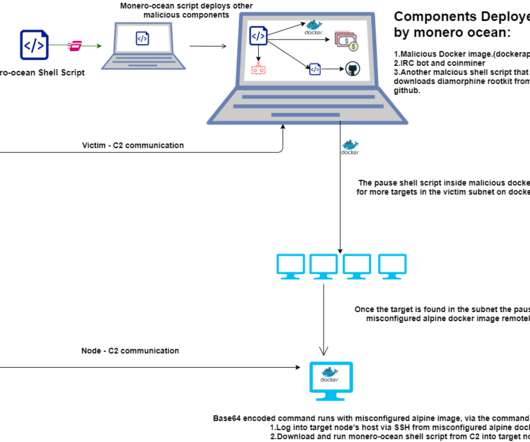
The financially motivated TeamTNT hacking group expanded its arsenal with new tools used to target thousands of victims worldwide. In January 2021, the cybercrime gang launched a new campaign targeting Kubernetes environments with the Hildegard malware. SecurityAffairs – hacking, TeamTNT). Pierluigi Paganini.




























Let's personalize your content