TeamTNT cybercrime gang expands its arsenal to target thousands of orgs worldwide
Security Affairs
SEPTEMBER 9, 2021
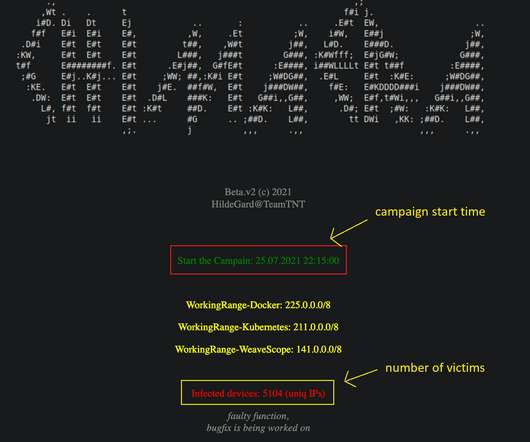
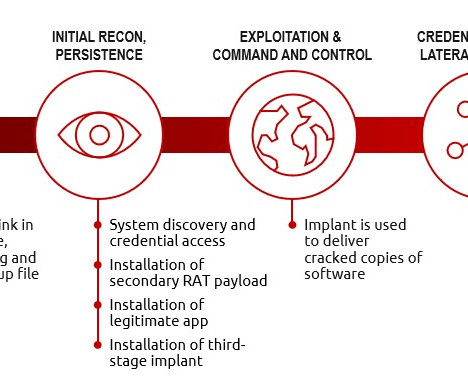
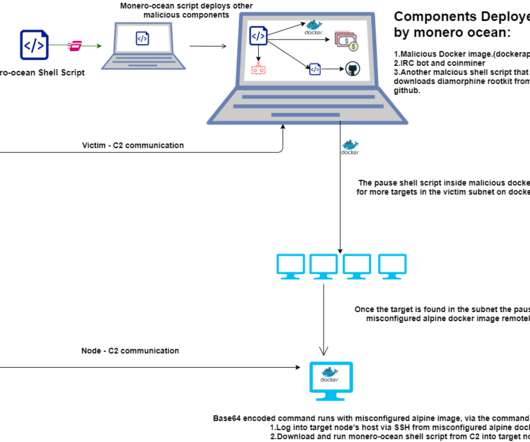
The activity of the TeamTNT group has been detailed by security firm Trend Micro, but in August 2020 experts from Cado Security discovered that that botnet is also able to target misconfigured Kubernetes installations. “AT&T Alien Labs has discovered new malicious files distributed by the threat actor TeamTNT. .





























Let's personalize your content