TA547 targets German organizations with Rhadamanthys malware
Security Affairs
APRIL 12, 2024
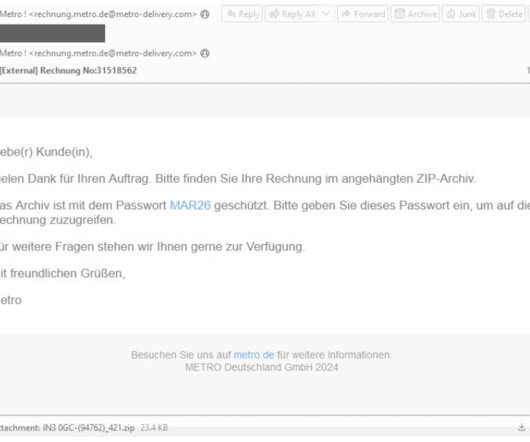
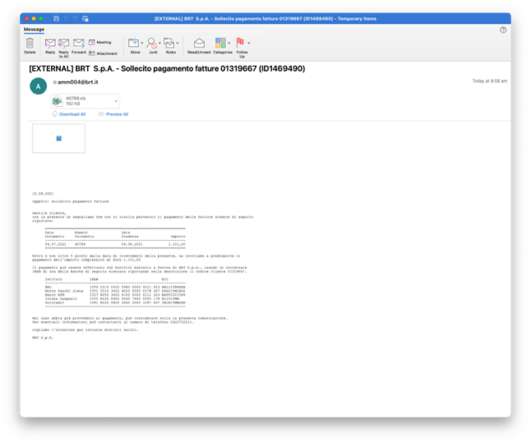
Proofpoint researchers observed a threat actor, tracked as TA547, targeting German organizations with an email campaign delivering the Rhadamanthys malware. The security firm pointed out that this is the first TA547 group to use this malware family. The experts also discovered the attempts of using LLM in malware campaigns.



























Let's personalize your content