FBI: Spike in Hacked Police Emails, Fake Subpoenas
Krebs on Security
NOVEMBER 9, 2024
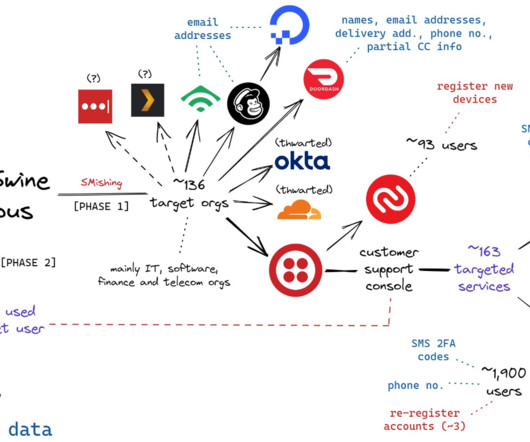
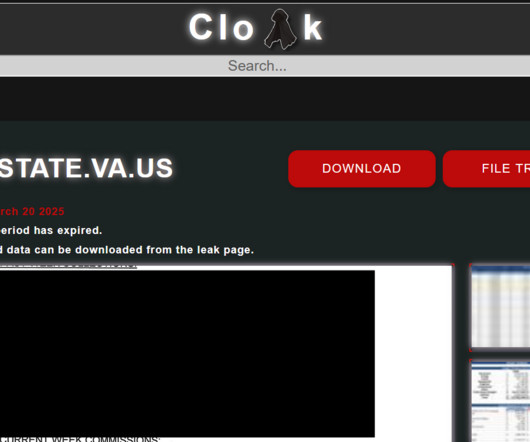
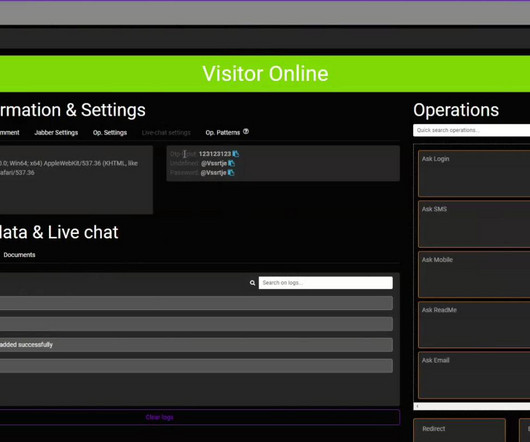
based technology companies. One English-speaking cybercriminal who goes by the nicknames “ Pwnstar ” and “ Pwnipotent ” has been selling fake EDR services on both Russian-language and English cybercrime forums. “This is social engineering at the highest level and there will be failed attempts at times. .
















































Let's personalize your content