NSFOCUS Innovative DDoS Protection Technology Secures Your Network Perimeter
Security Boulevard
FEBRUARY 22, 2024
Cybersecurity is crucial for national security in the digital world, where major powers clash over their interests. However, technology also enables more sophisticated and harmful network attacks. The post NSFOCUS Innovative DDoS Protection Technology Secures Your Network Perimeter appeared first on Security Boulevard.











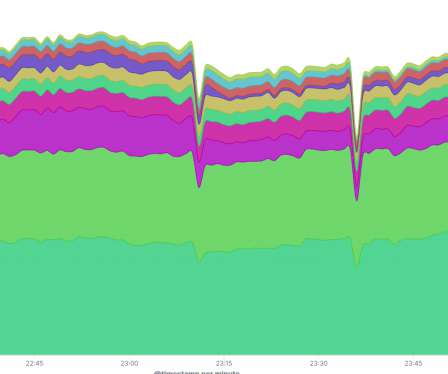





















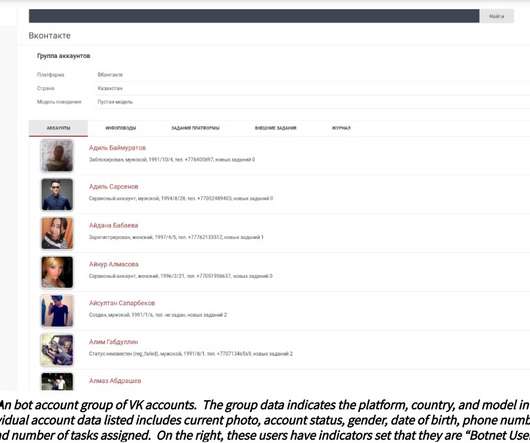















Let's personalize your content