Identity theft of 225,000 customers takes place at Latitude Financial Services
CyberSecurity Insiders
MARCH 15, 2023
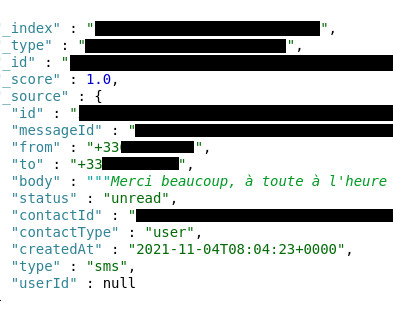
Note 1- Usually, hackers are always in lookout for such info, as they can stitch all these bits and pieces of data, to create a user profile and launch phishing or any other type of social engineering attack.
















































Let's personalize your content