Security Affairs newsletter Round 462 by Pierluigi Paganini – INTERNATIONAL EDITION
Security Affairs
MARCH 10, 2024
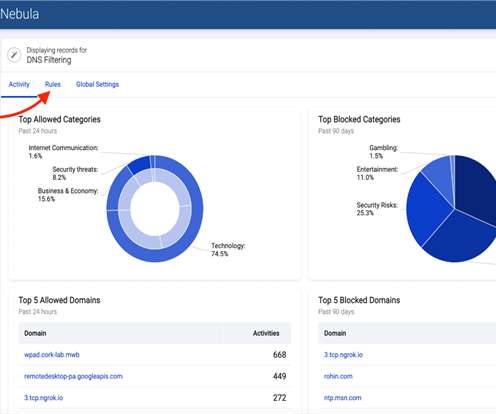
Judge ordered NSO Group to hand over the Pegasus spyware code to WhatsApp Cybercrime BlackCat Ransomware Affiliate TTPs American Express credit cards EXPOSED in third-party vendor data breach – account numbers and names among details accessed in hack LockBit 3.0’S

















































Let's personalize your content