Widespread exploitation by botnet operators of Zyxel firewall flaw
Security Affairs
JUNE 1, 2023
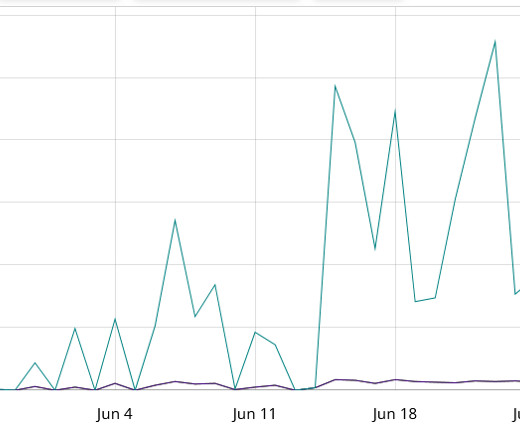
Threat actors are actively exploiting a command injection flaw, tracked as CVE-2023-28771, in Zyxel firewalls to install malware. Threat actors are actively attempting to exploit a command injection vulnerability, tracked as CVE-2023-28771 , that impacts Zyxel firewalls. in its firewall devices. VPN ZLD V4.60


















































Let's personalize your content