News alert: Gcore Radar reveals 56% rise in DDoS attacks – gaming industry targeted the most
The Last Watchdog
FEBRUARY 11, 2025
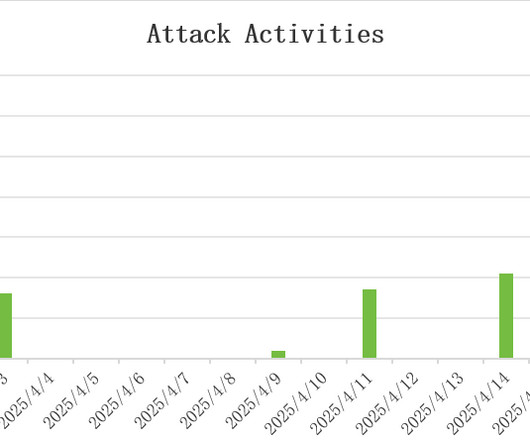
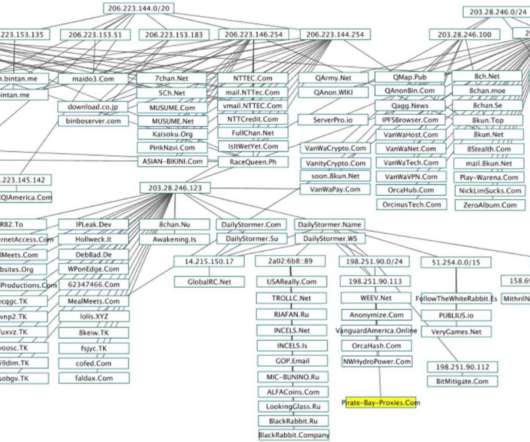
11, 2025, CyberNewswire — Gcore , the global edge AI, cloud, network, and security solutions provider, today announced the findings of its Q3-Q4 2024 Radar report into DDoS attack trends. DDoS attacks have reached unprecedented scale and disruption in 2024, and businesses need to act fast to protect themselves from this evolving threat.







































Let's personalize your content