Report: Recent 10x Increase in Cyberattacks on Ukraine
Krebs on Security
MARCH 11, 2022
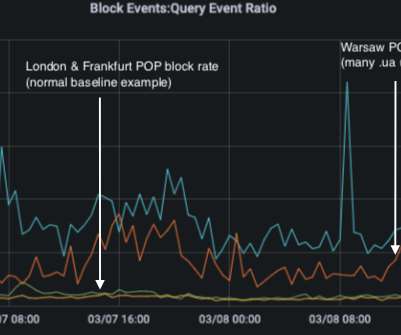
John Todd is general manager of Quad9 , a free “anycast” DNS platform. DNS stands for Domain Name System, which is like a globally distributed phone book for the Internet that maps human-friendly website names (example.com) to numeric Internet addresses (8.8.4.4.) Of those 121 million events, 4.6

















































Let's personalize your content