Check your DNS! Abandoned domains used to bypass spam checks
Malwarebytes
MARCH 5, 2024
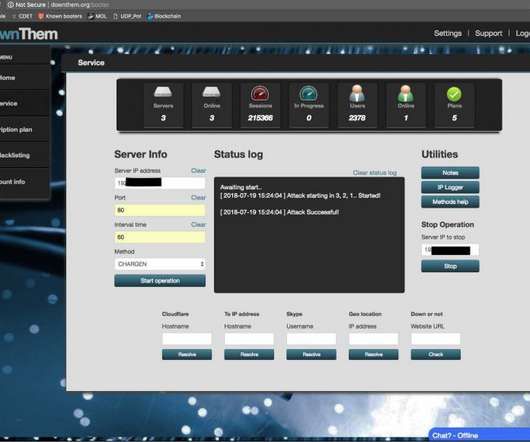
Companies use subdomains for all kinds of purposes, from differentiating marketing campaigns to naming different online systems. It’s also common practice for companies to create CNAME (Canonical Name) DNS records that alias a subdomain to another domain or subdomain.











































Let's personalize your content