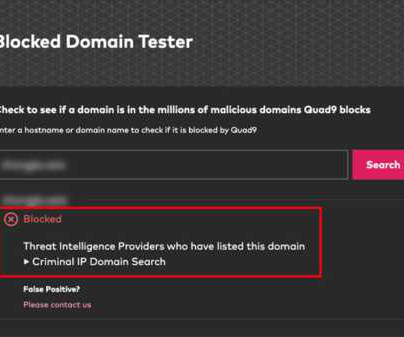
News alert: Criminal IP and Quad9 collaborate to exchange domain and IP threat intelligence
The Last Watchdog
MAY 13, 2024
This process not only safeguards computers, mobile devices, and IoT systems from a diverse array of threats like malware, phishing, spyware, and botnets, ensuring privacy, but also optimizes performance. Media contact : Michael Sena, AI SPERA, support@aispera.com




















Let's personalize your content