How IT teams can prevent phishing attacks with Malwarebytes DNS filtering
Malwarebytes
AUGUST 18, 2022
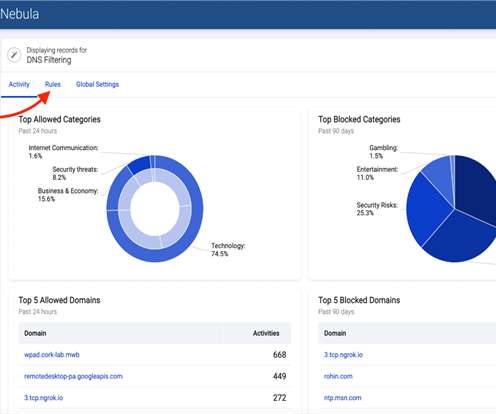
Phishing attacks are a persistent threat to businesses globally. According to Verizon , 82 percent of data breaches in 2021 involved the human element—with phishing attacks making up over 60 precent of these. With Malwarebytes DNS filtering , however, you can prevent a large swath of phishing attacks.






















Let's personalize your content