Duo vs. Fraudulent Device Registration
Duo's Security Blog
APRIL 8, 2024
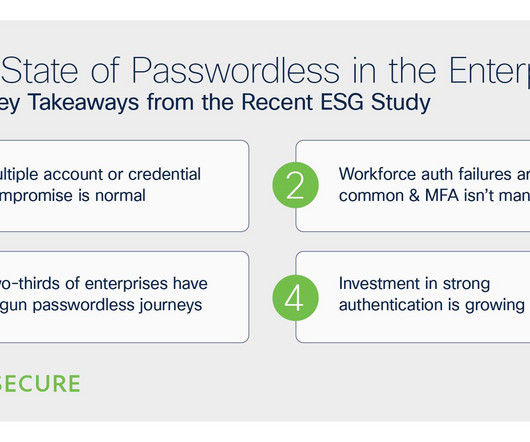
It is a well-known and established point that a password alone is not enough to secure an account. Risk-Based Authentication: Risk-Based Authentication can detect patterns from attackers and step up the authentication requirements to more secure factors in unknown or risky situations.
































Let's personalize your content