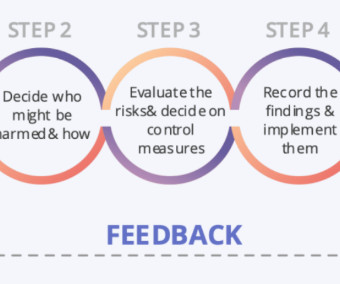
[eBook] A Step-by-Step Guide to Cyber Risk Assessment
The Hacker News
APRIL 11, 2023
In today's perilous cyber risk landscape, CISOs and CIOs must defend their organizations against relentless cyber threats, including ransomware, phishing, attacks on infrastructure, supply chain breaches, malicious insiders, and much more. One of the most effective ways for CISOs and

















































Let's personalize your content