What is IBM Hybrid Cloud Mesh?
Tech Republic Security
MAY 18, 2023
Learn what the expanded cloud offerings mean for potentially smoothing out the line between DevOps and SecOps. The post What is IBM Hybrid Cloud Mesh? appeared first on TechRepublic.

Tech Republic Security
MAY 18, 2023
Learn what the expanded cloud offerings mean for potentially smoothing out the line between DevOps and SecOps. The post What is IBM Hybrid Cloud Mesh? appeared first on TechRepublic.

The Last Watchdog
MAY 18, 2023
Your go-to mobile apps aren’t nearly has hackproof as you might like to believe. Related: Fallout of T-Mobile hack Hackers of modest skill routinely bypass legacy security measures, even two-factor authentication, with techniques such as overlay attacks. And hard data shows instances of such breaches on the rise. I had an evocative conversation about this at RSA Conference 2023 with Asaf Ashkenazi , CEO of Verimatrix , a cybersecurity company headquartered in southern France.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
MAY 18, 2023
The single sign-on market leader’s Security Center, now generally available, uses Okta Customer Identity Cloud for insights into authentication activity for insights into anomalies, threats and security friction. The post Okta’s Security Center opens window to customer insights, including threats and friction appeared first on TechRepublic.

Bleeping Computer
MAY 18, 2023
The popular KeePass password manager is vulnerable to extracting the master password from the application's memory, allowing attackers who compromise a device to retrieve the password even with the database is locked. [.

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.

Tech Republic Security
MAY 18, 2023
Jack Wallen demonstrates how to scan container images for vulnerabilities and dependencies with the new Docker Scout feature. The post How to scan container images with Docker Scout appeared first on TechRepublic.

Dark Reading
MAY 18, 2023
Cybercrime group that often uses smishing for initial access bypassed traditional OS targeting and evasion techniques to directly gain access to the cloud.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Bleeping Computer
MAY 18, 2023
Hackers are now actively probing for vulnerable Essential Addons for Elementor plugin versions on thousands of WordPress websites in massive Internet scans, attempting to exploit a critical account password reset flaw disclosed earlier in the month. [.

Dark Reading
MAY 18, 2023
As ChatGPT adoption grows, the industry needs to proceed with caution. Here's why.

Bleeping Computer
MAY 18, 2023
Apple has addressed three new zero-day vulnerabilities exploited in attacks to hack into iPhones, Macs, and iPads. [.

Security Boulevard
MAY 18, 2023
ChatGPT has become a powerful tool for security professionals seeking to enrich their work. However, its widespread use has raised concerns about the potential for bad actors to misuse the technology. Experts are worried that ChatGPT’s ability to source recent data about an organization could make social engineering and phishing attacks more effective than ever.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Dark Reading
MAY 18, 2023
A newly discovered bug in the open source password manager, if exploited, lets attackers retrieve a target's master password — and proof-of-concept code is available.

Bleeping Computer
MAY 18, 2023
A cybercriminal tracked as the "Lemon Group" has been infecting millions of Android-based smartphones, watches, TVs, and TV boxes, with a malware strain named 'Guerilla.' [.

Veracode Security
MAY 18, 2023
I look back on L0pht’s testimony before Congress in 1998 with a mix of pride and reflection. It’s been twenty-five years since our group of hackers (or vulnerability researchers, if you will) stepped up to raise awareness about the importance of internet security in front of some of the world’s most powerful lawmakers. This event marked the beginning of a long journey towards increased cybersecurity awareness and implementation of measures to protect our digital world.

Dark Reading
MAY 18, 2023
Turkorat-poisoned packages sat in the npm development library for months, researchers say.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

CyberSecurity Insiders
MAY 18, 2023
To all those who are eagerly searching for ChatGPT login and Midjourney web pages, here’s an alert that needs your immediate attention. A threat actor named BatLoader has started a campaign of hosting fake ChatGPT and Midjourney webpages on Google ads. So, next time when you search for the said web portals, be sure of what you’re clicking on and do not input your login credentials blindly!

Dark Reading
MAY 18, 2023
Plug X and other information-stealing remote-access Trojans are among the malware targeting networking, manufacturing, and logistics companies in Taiwan.
The Hacker News
MAY 18, 2023
Apple on Thursday rolled out security updates to iOS, iPadOS, macOS, tvOS, watchOS, and the Safari web browser to address three new zero-day flaws that it said are being actively exploited in the wild. The three security shortcomings are listed below - CVE-2023-32409 - A WebKit flaw that could be exploited by a malicious actor to break out of the Web Content sandbox.

We Live Security
MAY 18, 2023
A roundup of some of the handiest tools that security professionals can use to search for and monitor devices that are accessible from the internet The post 5 useful search engines for internet‑connected devices and services appeared first on WeLiveSecurity

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.
The Hacker News
MAY 18, 2023
Malicious Google Search ads for generative AI services like OpenAI ChatGPT and Midjourney are being used to direct users to sketchy websites as part of a BATLOADER campaign designed to deliver RedLine Stealer malware. "Both AI services are extremely popular but lack first-party standalone apps (i.e.

Trend Micro
MAY 18, 2023
This is the first part of our security analysis of an information stealer targeting GitHub Codespaces (CS) that discusses how attackers can abuse these cloud services for a variety of malicious activities.

Naked Security
MAY 18, 2023
Laugh (sufficiently), learn (efficiently), and then let us know what you think in our comments (anonymously, if you wish).

PCI perspectives
MAY 18, 2023
The clock is ticking on PCI DSS v3.2.1. On 31 March 2024, PCI DSS v3.2.1 will be retired, making the transition to PCI DSS v4.0 essential for organizations involved in payment data security. To help with this transition, PCI SSC has identified eight steps you should take on your journey to PCI DSS v4.0.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Dark Reading
MAY 18, 2023
Risk from artificial intelligence vectors presents a growing concern among security professionals in 2023.

Naked Security
MAY 18, 2023
All Apple users have zero-days that need patching, though some have more zero-days than others.

CSO Magazine
MAY 18, 2023
While most organizations have a cyber resilience program in place, more than half of them lack a comprehensive approach to assessing resilience, according to a study by Immersive Labs. The study aimed at understanding business preparedness amidst growing incidents found a strong intent to strengthen cybersecurity capabilities driven by external threats.

CyberSecurity Insiders
MAY 18, 2023
A threat actor with a history of targeting Microsoft servers has recently gained control over virtual machines (VMs) and installed third-party remote management software within clients’ cloud environments. The Mandiant Intelligence team has identified this actor, known as UNC3844, evading security software detections on Azure cloud platforms. Their primary objective is to exploit cloud storage spaces, steal valuable data for financial gain, and potentially threaten victims through data ext

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.
The Hacker News
MAY 18, 2023
A cybercrime enterprise known as Lemon Group is leveraging millions of pre-infected Android smartphones worldwide to carry out their malicious operations, posing significant supply chain risks.
Security Boulevard
MAY 18, 2023
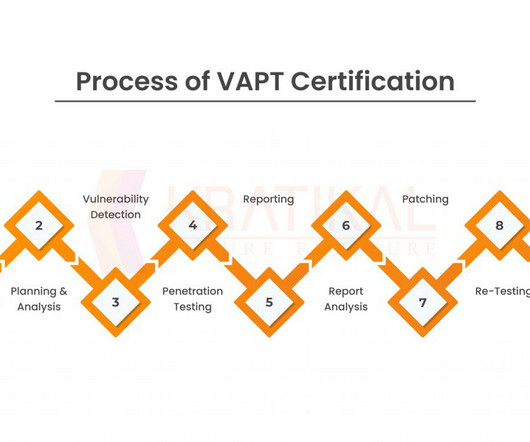
Introduction Making sure our internet systems and data are secure has become crucial in today’s digital world, as technology is ingrained in every part of our lives. Organizations of all sizes are frequently vulnerable to a variety of cyber dangers. A thorough strategy that incorporates Vulnerability Assessment and Penetration Testing (VAPT) is essential for reducing […] The post “VAPT: The Shield Your Organization Needs Against Cyber Threats” appeared first on Kratikal Blogs.

CyberSecurity Insiders
MAY 18, 2023
In today’s digital age, profit-making organizations across industries are increasingly reliant on technology and the internet to conduct their operations. While this technological advancement brings numerous benefits, it also exposes businesses to various cybersecurity risks. Protecting sensitive data, customer information, financial records, and intellectual property has become a critical priority.

eSecurity Planet
MAY 18, 2023
Cisco is warning that nine significant vulnerabilities in its Small Business Series Switches could enable unauthenticated remote attackers to cause a denial-of-service condition or execute arbitrary code with root privileges on affected devices. The vulnerabilities are caused by improper validation of requests sent to the switches’ web interfaces, the company said.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
Let's personalize your content