How to Check If Someone Else Accessed Your Google Account
Tech Republic Security
JULY 14, 2023
Review your recent Gmail access, browser sign-in history and Google account activity to make sure no one other than you has used your account.
Tech Republic Security
JULY 14, 2023
Review your recent Gmail access, browser sign-in history and Google account activity to make sure no one other than you has used your account.
Bleeping Computer
JULY 14, 2023
In what is shaping up to be a widespread privacy controversy, Spotify has come under scrutiny following allegations by users that the music streaming service made their private playlists public without their consent. [.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
JULY 14, 2023
The White House has announced the first iteration of the National Cybersecurity Implementation Plan. Read on to learn more about the plan and alignment with the five essential pillars.

Security Boulevard
JULY 14, 2023
A SlashNext report detailed how cybercriminals use generative AI capabilities to launch phishing and BEC attacks in greater volume. The post SlashNext Report Shows How Cybercriminals Use Generative AI appeared first on Security Boulevard.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Tech Republic Security
JULY 14, 2023
The Scarleteel threat targets AWS Fargate environments for data theft and more malicious types of attacks such as cryptojacking and DDoS. Learn how to mitigate this threat.

Security Boulevard
JULY 14, 2023
This time every year, Las Vegas transforms into the epicenter of the security world with a lineup of major industry events – Black Hat, BSides and DEFCON. Rezilion is excited to be taking part in all three events in 2023. Here’s a look at what we have planned – and how you can join us. Join Rezilion in Las Vegas for Black Hat, BSides and DEFCON, 2023 The post Join Rezilion in Las Vegas for Black Hat, BSides and DEFCON, 2023 appeared first on Rezilion.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Security Boulevard
JULY 14, 2023
Our thanks to BSides Sofia for publishing their presenter’s tremendous BSides Sofia 2023 content on the organizations’ YouTube channel. Permalink The post BSides Sofia 2023 – Deputy Minister Atanas Maznev e-Government, Rosen Kirilov, PhD, UNWE – Conference Opening appeared first on Security Boulevard.

Bleeping Computer
JULY 14, 2023
Microsoft says it still doesn't know how Chinese hackers stole an inactive Microsoft account (MSA) consumer signing key used to breach the Exchange Online and Azure AD accounts of two dozen organizations, including government agencies. [.

Malwarebytes
JULY 14, 2023
A group of seven US senators has sent a letter to the heads of the IRS, the Department of Justice, the Federal Trade Commission and the IRS watchdog, revealing that they have found evidence that reveals “a shocking breach of taxpayer privacy by tax prep companies and by Big Tech firms.” According to the letter, information about tens of millions of US taxpayers was sent by three tax preparation firms to social media giant Meta.
Security Affairs
JULY 14, 2023
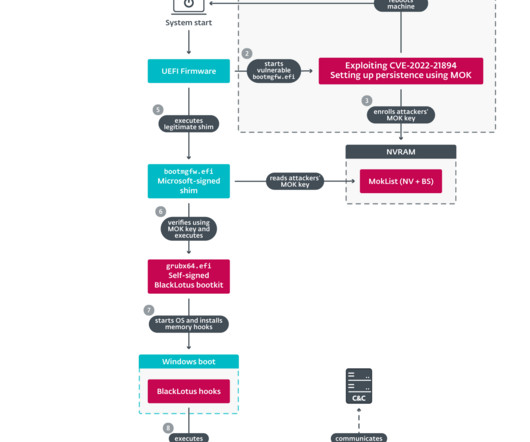
The source code for the BlackLotus UEFI bootkit has been published on GitHub and experts warn of the risks of proliferation of custom versions. Researchers from ESET discovered in March a new stealthy Unified Extensible Firmware Interface ( UEFI ) bootkit, named BlackLotus , that is able to bypass Secure Boot on Windows 11. Secure Boot is a security feature of the latest Unified Extensible Firmware Interface (UEFI) 2.3.1 designed to detect tampering with boot loaders, key operating system fi

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Security Boulevard
JULY 14, 2023
How can organizations take a proactive approach to cybersecurity privilege creep? Cybersecurity isn’t just about defending against external threats; it’s equally about managing internal vulnerabilities. Cybersecurity ‘privilege creep’ is a term used to describe the gradual accumulation of access rights beyond what an individual needs to perform their job.

The Hacker News
JULY 14, 2023
Microsoft on Friday said a validation error in its source code allowed for Azure Active Directory (Azure AD) tokens to be forged by a malicious actor known as Storm-0558 using a Microsoft account (MSA) consumer signing key to breach two dozen organizations.

Security Boulevard
JULY 14, 2023
Conducting regular penetration tests (pentests) is a proactive option that identifies, evaluates and mitigates risks. The post Why Pentesting-as-a-Service is Vital for Business Security appeared first on Security Boulevard.

TrustArc
JULY 14, 2023
TrustArc’s privacy experts review the implications of new personal information privacy rules in the Washington My Health My Data Act, and how its private right of action could trigger waves of litigation. The post Washington My Health My Data Act: Implications appeared first on TrustArc Privacy Blog.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Security Boulevard
JULY 14, 2023
Identity-based attacks are a growing concern for organizations of all sizes and industries. Here’s how to protect yourself. The post 3 Ways To Build A Stronger Approach to Identity Protection appeared first on Security Boulevard.
The Hacker News
JULY 14, 2023
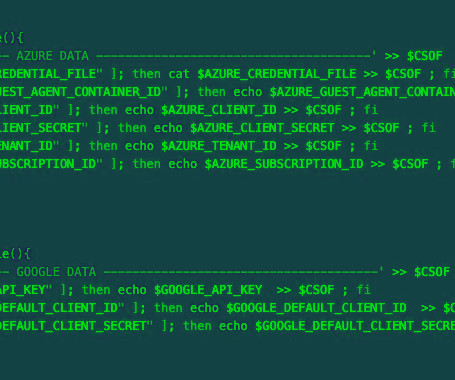
A malicious actor has been linked to a cloud credential stealing campaign in June 2023 that's focused on Azure and Google Cloud Platform (GCP) services, marking the adversary's expansion in targeting beyond Amazon Web Services (AWS).
Security Boulevard
JULY 14, 2023
via the inimitable Daniel Stori , crafting superb comics at turnoff.us ! Permalink The post Daniel Stori’s ‘chown – chmod’ appeared first on Security Boulevard.

The Hacker News
JULY 14, 2023
Zimbra has warned of a critical zero-day security flaw in its email software that has come under active exploitation in the wild. "A security vulnerability in Zimbra Collaboration Suite Version 8.8.15 that could potentially impact the confidentiality and integrity of your data has surfaced," the company said in an advisory.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.
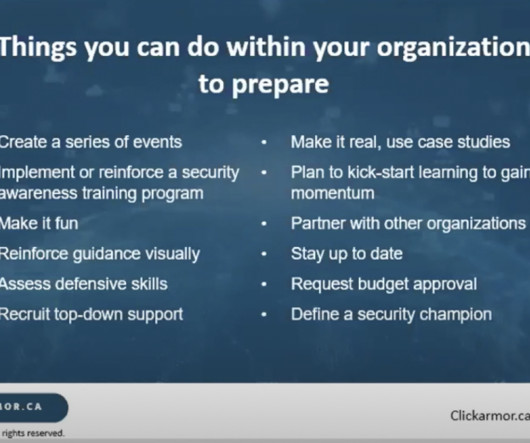
Security Boulevard
JULY 14, 2023
The post Preparing for Cyber Security Awareness Month appeared first on Click Armor. The post Preparing for Cyber Security Awareness Month appeared first on Security Boulevard.
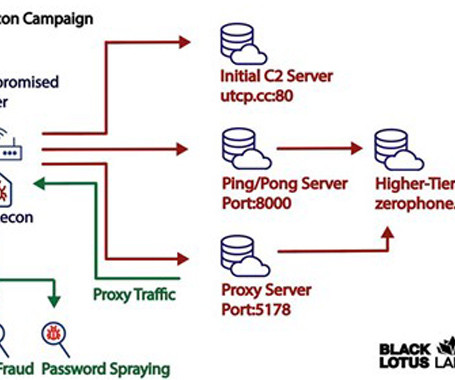
The Hacker News
JULY 14, 2023
A new malware strain has been found covertly targeting small office/home office (SOHO) routers for more than two years, infiltrating over 70,000 devices and creating a botnet with 40,000 nodes spanning 20 countries. Lumen Black Lotus Labs has dubbed the malware AVrecon, making it the third such strain to focus on SOHO routers after ZuoRAT and HiatusRAT over the past year.

Security Boulevard
JULY 14, 2023
After a ransomware attack shuttered operations at container terminals at the Port of Nagoya in Japan, the Lockbit 3.0 ransomware gang claimed responsibility and demanded the port pay up. The attack on the port, which is responsible for 10% of the country’s cargo trade and is used by companies like Toyota Motor Corporation, was attacked. The post Lockbit 3.0 Claims Credit for Ransomware Attack on Japanese Port appeared first on Security Boulevard.

The Hacker News
JULY 14, 2023
All-In-One Security (AIOS), a WordPress plugin installed on over one million sites, has issued a security update after a bug introduced in version 5.1.9 of the software caused users' passwords being added to the database in plaintext format. "A malicious site administrator (i.e.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

Security Boulevard
JULY 14, 2023
Our thanks to BSides Sofia for publishing their presenter’s tremendous BSides Sofia 2023 content on the organizations’ YouTube channel. Permalink The post BSides Sofia 2023 Intro appeared first on Security Boulevard.

SecureBlitz
JULY 14, 2023
Learn how to set up the ideal gaming room for E-Sport competitions. In the ever-evolving landscape of e-Sports, having a tailored gaming room is as crucial as the skills you bring into the virtual arena. Like a finely tuned race car, your gaming setup can directly impact your performance during competition. Consider this: just as […] The post How To Set Up The Ideal Gaming Room For E-Sport Competitions appeared first on SecureBlitz Cybersecurity.
Security Boulevard
JULY 14, 2023
The post Multi-layered Defense: Enhancing Security with Fidelis Active Directory Intercept™ appeared first on Fidelis Cybersecurity. The post Multi-layered Defense: Enhancing Security with Fidelis Active Directory Intercept™ appeared first on Security Boulevard.

Bleeping Computer
JULY 14, 2023
Colorado State University (CSU) has confirmed that the Clop ransomware operation stole sensitive personal information of current and former students and employees during the recent MOVEit Transfer data-theft attacks. [.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Security Boulevard
JULY 14, 2023
Imagine yourself on a cross-country road trip. You have a full tank of gas, plenty of snacks, the radio is tuned to your favorite station, and you know exactly where you’re going. The only problem? You don’t know how to get there. There are plenty of twists and turns along the way, and if you’re […] The post A K-12 Guide to Incident Response Plans, Challenges, and Frameworks appeared first on ManagedMethods.

Bleeping Computer
JULY 14, 2023
Rockwell Automation says a new remote code execution (RCE) exploit linked to an unnamed Advanced Persistent Threat (APT) group could be used to target unpatched ControlLogix communications modules commonly used in manufacturing, electric, oil and gas, and liquified natural gas industries. [.

Graham Cluley
JULY 14, 2023
A federal grand jury has indicted a former employee of a contractor operating a California town's wastewater treatment facility, alleging that he remotely turned off critical systems and could have endangered public health and safety. Read more in my article on the Tripwire State of Security blog.
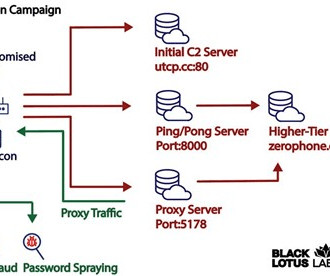
Security Affairs
JULY 14, 2023
A new malware dubbed AVrecon targets small office/home office (SOHO) routers, it infected over 70,000 devices from 20 countries. Lumen Black Lotus Labs uncovered a long-running hacking campaign targeting SOHO routers with a strain of malware dubbed AVrecon. The malware was spotted the first time in May 2021, but has been operating under the radar for more than two years. “Lumen Black Lotus Labs identified another multi-year campaign involving compromised routers across the globe.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content