The AI Attack Surface Map v1.0
Daniel Miessler
MAY 15, 2023
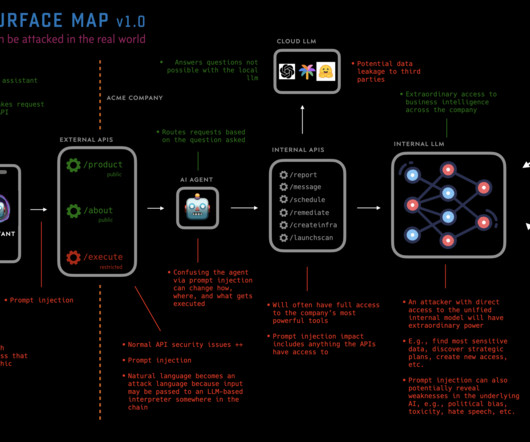
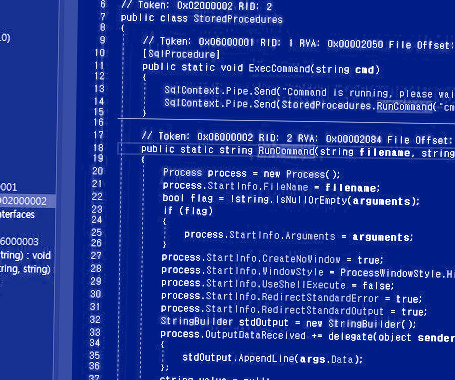
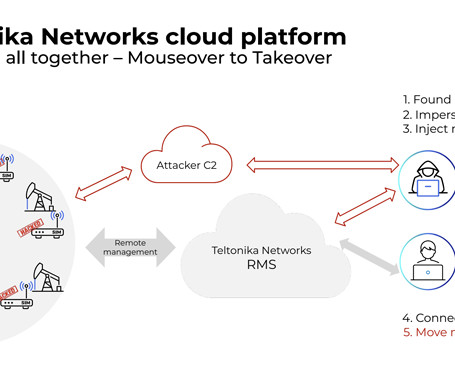
Introduction Purpose Components Attacks Discussion Summary Introduction This resource is a first thrust at a framework for thinking about how to attack AI systems. At the time of writing, GPT-4 has only been out for a couple of months, and ChatGPT for only 6 months. So things are very early. There has been, of course, much content on attacking pre-ChatGPT AI systems, namely how to attack machine learning implementations.








































Let's personalize your content