Parmesan Anti-Forgery Protection
Schneier on Security
AUGUST 24, 2023
The Guardian is reporting about microchips in wheels of Parmesan cheese as an anti-forgery measure.

Schneier on Security
AUGUST 24, 2023
The Guardian is reporting about microchips in wheels of Parmesan cheese as an anti-forgery measure.

Tech Republic Security
AUGUST 24, 2023
This QR code phishing campaign is targeting multiple industries and using legitimate services such as Microsoft Bing to increase its efficiency and bypass security.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
AUGUST 24, 2023
Tel Aviv, Israel, Aug. 24, 2023 – Cypago announced the release of its Cyber GRC Automation (CGA) platform today, revolutionizing the GRC space by bridging the gap between management, security, and operations teams. This announcement follows the company’s $13M in total funding led by Entrée Capital, Axon Ventures, and Jump Capital, including prominent angel investors such as Ariel Maislos, Prof.
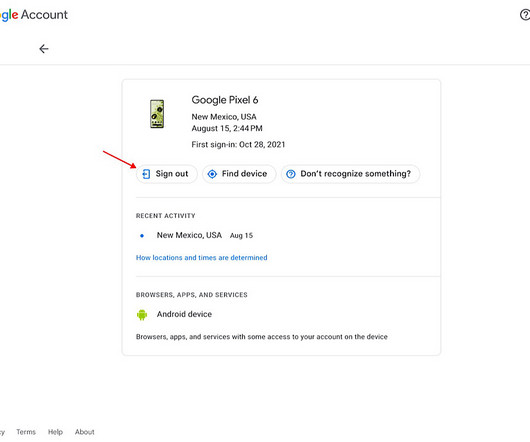
Tech Republic Security
AUGUST 24, 2023
Follow this guide to learn how to easily remove any device from your Google account and keep your account secure.

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.
Cisco Security
AUGUST 24, 2023
A deployment guide for wireless ThousandEyes agents deployed to monitor the Black Hat 2023 conference by Adam Kilgore & Ryan MacLennan ThousandEyes (TE) Black Hat 2023 Deployment Guide This guide documents the setup and installation procedures used to deploy ThousandEyes at Black Hat 2023. This document covers configuration of the TE agent on Raspberry Pi 4, including both wired and wireless configurations.

Tech Republic Security
AUGUST 24, 2023
Google announced security enhancements to Google Workspace focused on enhancing threat defense controls with Google AI.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Tech Republic Security
AUGUST 24, 2023
A new study by Critical Insight shows that cybersecurity attacks in the health care sector are hitting more individuals and finding vulnerabilities in third-party partners.

Bleeping Computer
AUGUST 24, 2023
Microsoft says the August 2023 preview updates released this week for Windows 11 and Windows 10 systems are causing blue screens with errors mentioning an unsupported processor issue.

The Hacker News
AUGUST 24, 2023
Thousands of Openfire XMPP servers are unpatched against a recently disclosed high-severity flaw and are susceptible to a new exploit, according to a new report from VulnCheck. Tracked as CVE-2023-32315 (CVSS score: 7.
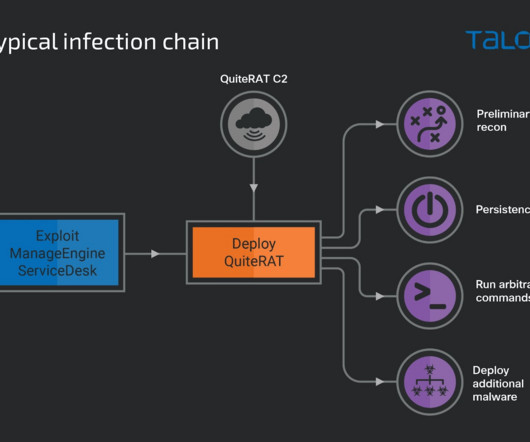
Security Affairs
AUGUST 24, 2023
The North Korea-linked Lazarus group exploits a critical flaw in Zoho ManageEngine ServiceDesk Plus to deliver the QuiteRAT malware. The North Korea-linked APT group Lazarus has been exploiting a critical vulnerability, tracked as CVE-2022-47966 , in Zoho’s ManageEngine ServiceDesk in attacks aimed at the Internet backbone infrastructure provider and healthcare organizations.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Security Boulevard
AUGUST 24, 2023
It's time to ask tough questions and carefully scrutinize new cybersecurity tools before pulling the trigger on purchases. The post Do we really need another cybersecurity tool? appeared first on SafeBreach. The post Do we really need another cybersecurity tool? appeared first on Security Boulevard.
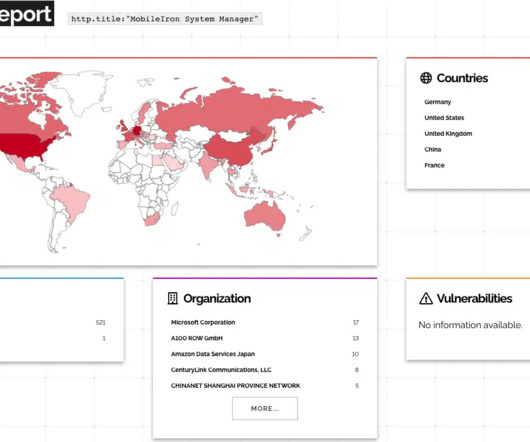
Security Affairs
AUGUST 24, 2023
Proof-of-concept exploit code for critical Ivanti Sentry authentication bypass flaw CVE-2023-38035 has been released. Researchers released a proof-of-concept (PoC) exploit code for critical Ivanti Sentry authentication bypass vulnerability CVE-2023-38035 (CVSS score 9.8). This week the software company Ivanti released urgent security patches to address the critical-severity vulnerability CVE-2023-38035 impacting the Ivanti Sentry (formerly MobileIron Sentry) product.

The Hacker News
AUGUST 24, 2023
Public Wi-Fi, which has long since become the norm, poses threats to not only individual users but also businesses. With the rise of remote work, people can now work from virtually anywhere: a cafe close to home, a hotel in a different city, or even while waiting for a plane at the airport. Next, let's explore the risks of connecting to public Wi-Fi, both for you personally and for businesses.
Security Affairs
AUGUST 24, 2023
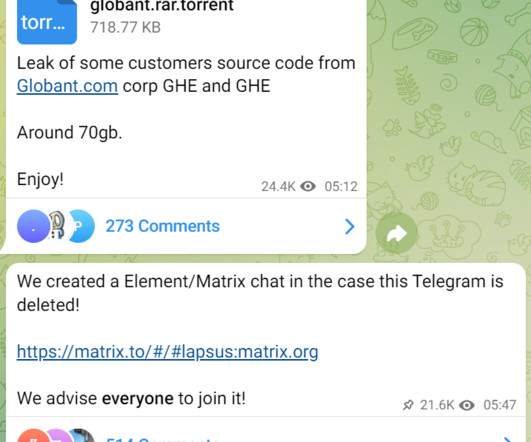
An 18-year-old member of the Lapsus$ gang has been convicted of having helped hack multiple high-profile companies. A teenage member of the Lapsus$ data extortion group, Arion Kurtaj (18), was convicted by a London jury of having hacked multiple high-profile companies, including Uber , Revolut , and blackmailed the developers of the gaming firm Rockstar Games.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Security Boulevard
AUGUST 24, 2023
Arion Kurtaj and anon minor: Part of group that hacked Uber, Nvidia, Microsoft, Rockstar Games and many more. The post Lapsus$ Jury Says Teen Duo Did Do Crimes appeared first on Security Boulevard.

Security Affairs
AUGUST 24, 2023
The FBI warned that patches for a critical Barracuda ESG flaw CVE-2023-2868 are “ineffective” and patched appliances are still being hacked. The Federal Bureau of Investigation warned that security patches for critical vulnerability CVE-2023-2868 in Barracuda Email Security Gateway (ESG) are “ineffective.” According to the feds, threat actors are still hacking the patched appliances in ongoing hacking campaigns.
The Hacker News
AUGUST 24, 2023
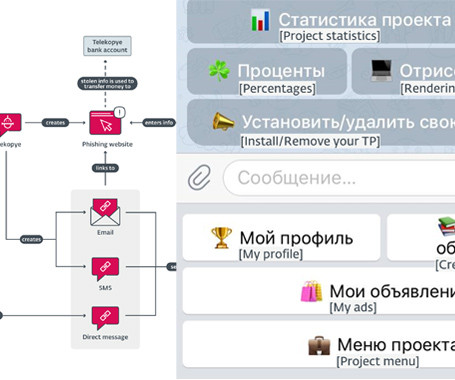
A new financially motivated operation is leveraging a malicious Telegram bot to help threat actors scam their victims. Dubbed Telekopye, a portmanteau of Telegram and kopye (meaning "spear" in Russian), the toolkit functions as an automated means to create a phishing web page from a premade template and send the URL to potential victims, codenamed Mammoths by the criminals.

Heimadal Security
AUGUST 24, 2023
Hey there, fellow digital explorers! Welcome to a journey that promises to take your cybersecurity understanding to a whole new dimension. As the Stellar Strategist of Product Prowess (Head of Product Marketing) at Heimdal, I’m excited to guide you through the cosmic wonders of Heimdal XDR, an innovation that’s poised to transform the cybersecurity landscape. […] The post Into the Heimdalverse appeared first on Heimdal Security Blog.

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.

SecureBlitz
AUGUST 24, 2023
What is the average cost of a laptop? Here is the answer. In today's world, computers have become an indispensable part of our everyday lives. They serve as invaluable tools for work, communication, entertainment, and so much more. However, when it comes to purchasing, the average cost of a laptop can vary greatly depending on […] The post What Is The Average Cost Of A Laptop?

SecureWorld News
AUGUST 24, 2023
The U.S. government has issued a warning to private space companies that foreign entities are actively trying to infiltrate and steal sensitive technologies and data from America's booming space industry. In an advisory published last week , the FBI, National Counterintelligence and Security Center, and Air Force Office of Special Investigations cautioned that hackers backed by foreign governments are utilizing an array of tactics to gain access to American space organizations.

Heimadal Security
AUGUST 24, 2023
The University of Minnesota is currently conducting an investigation into a substantial data breach that could potentially impact a large number of alumni and members of the university community. Millions Potentially Exposed The breach was brought to light last month when an unauthorized party claimed to have gained access to sensitive data stored within the […] The post University of Minnesota Reports Massive Data Breach appeared first on Heimdal Security Blog.
The Hacker News
AUGUST 24, 2023
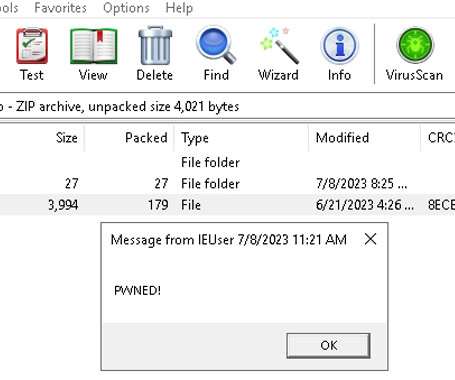
A recently patched security flaw in the popular WinRAR archiving software has been exploited as a zero-day since April 2023, new findings from Group-IB reveal. The vulnerability, cataloged as CVE-2023-38831, allows threat actors to spoof file extensions, thereby making it possible to launch malicious scripts contained within an archive that masquerades as seemingly innocuous image or text files.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Heimadal Security
AUGUST 24, 2023
Over 3,000 Openfire servers have yet to be updated against a critical security vulnerability. Tracked as CVE-2023-32315, the flaw has been actively exploited for more than two months, putting unpatched servers at significant risk. Upon a Closer Look Openfire, a widely used cross-platform real-time collaboration server written in Java, has gained immense popularity due to […] The post Thousands of Openfire Servers at Risk from Critical CVE appeared first on Heimdal Security Blog.
The Hacker News
AUGUST 24, 2023
The SmokeLoader malware is being used to deliver a new Wi-Fi scanning malware strain called Whiffy Recon on compromised Windows machines. "The new malware strain has only one operation.

WIRED Threat Level
AUGUST 24, 2023
Musician Alex Pall spoke with WIRED about his VC firm, the importance of raising cybersecurity awareness in a rapidly digitizing world, and his surprise that hackers know how to go hard.
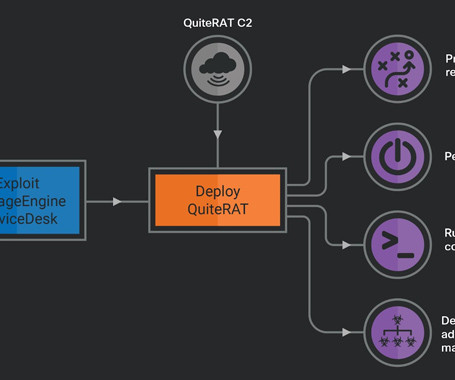
The Hacker News
AUGUST 24, 2023
The North Korea-linked threat actor known as Lazarus Group has been observed exploiting a now-patched critical security flaw impacting Zoho ManageEngine ServiceDesk Plus to distribute a remote access trojan called such as QuiteRAT. Targets include internet backbone infrastructure and healthcare entities in Europe and the U.S.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

WIRED Threat Level
AUGUST 24, 2023
Russia tightly controls its information space—making it hard to get accurate information out of the country. But open source data provides some clues about the crash.

Heimadal Security
AUGUST 24, 2023
Cyber-attacks can come in many forms. In the world of cybersecurity, the terms “ransomware” and “malware” are often used interchangeably, leading to confusion about their distinct characteristics and implications. While both ransomware and malware fall under the broader category of malicious software, they serve different purposes and have unique impacts on organizations and society.
SecureBlitz
AUGUST 24, 2023
Here, I will talk about sustainable finance and positive global transformation. In today's rapidly changing world, sustainability has evolved from a buzzword to a critical pillar of responsible business practices. As individuals and corporations alike recognize the urgent need to address environmental and social challenges, the realm of finance has not remained untouched.

The Hacker News
AUGUST 24, 2023
The U.S. Justice Department (DoJ) on Wednesday unsealed an indictment against two founders of the now-sanctioned Tornado Cash cryptocurrency mixer service, charging them with laundering more than $1 billion in criminal proceeds.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
Let's personalize your content