Parmesan Anti-Forgery Protection
Schneier on Security
AUGUST 24, 2023
The Guardian is reporting about microchips in wheels of Parmesan cheese as an anti-forgery measure.

Schneier on Security
AUGUST 24, 2023
The Guardian is reporting about microchips in wheels of Parmesan cheese as an anti-forgery measure.

Tech Republic Security
AUGUST 24, 2023
This QR code phishing campaign is targeting multiple industries and using legitimate services such as Microsoft Bing to increase its efficiency and bypass security.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Bleeping Computer
AUGUST 24, 2023
Microsoft says the August 2023 preview updates released this week for Windows 11 and Windows 10 systems are causing blue screens with errors mentioning an unsupported processor issue.

Tech Republic Security
AUGUST 24, 2023
A new study by Critical Insight shows that cybersecurity attacks in the health care sector are hitting more individuals and finding vulnerabilities in third-party partners.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Security Boulevard
AUGUST 24, 2023
It's time to ask tough questions and carefully scrutinize new cybersecurity tools before pulling the trigger on purchases. The post Do we really need another cybersecurity tool? appeared first on SafeBreach. The post Do we really need another cybersecurity tool? appeared first on Security Boulevard.
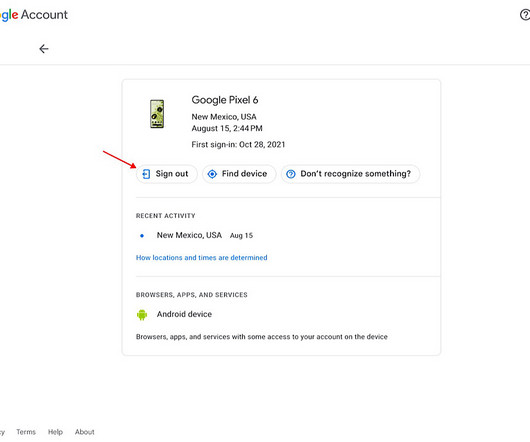
Tech Republic Security
AUGUST 24, 2023
Follow this guide to learn how to easily remove any device from your Google account and keep your account secure.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Tech Republic Security
AUGUST 24, 2023
Google announced security enhancements to Google Workspace focused on enhancing threat defense controls with Google AI.

Bleeping Computer
AUGUST 24, 2023
The North Korean state-backed hacker group tracked as Lazarus has been exploiting a critical vulnerability (CVE-2022-47966) in Zoho's ManageEngine ServiceDesk to compromise an internet backbone infrastructure provider and healthcare organizations. [.
Heimadal Security
AUGUST 24, 2023
CloudNordic and AzeroCloud, Danish hosting firms specializing in cloud services, have been hit hard by ransomware attacks, causing widespread data loss and operational disruptions. The companies are steadfast in their decision not to pay the ransom demanded by the hackers. Further Context The attack seems to have targeted servers during a data center migration.

The Hacker News
AUGUST 24, 2023
Thousands of Openfire XMPP servers are unpatched against a recently disclosed high-severity flaw and are susceptible to a new exploit, according to a new report from VulnCheck. Tracked as CVE-2023-32315 (CVSS score: 7.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.
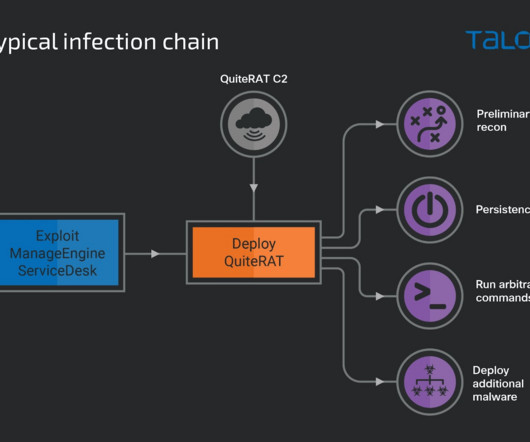
Security Affairs
AUGUST 24, 2023
The North Korea-linked Lazarus group exploits a critical flaw in Zoho ManageEngine ServiceDesk Plus to deliver the QuiteRAT malware. The North Korea-linked APT group Lazarus has been exploiting a critical vulnerability, tracked as CVE-2022-47966 , in Zoho’s ManageEngine ServiceDesk in attacks aimed at the Internet backbone infrastructure provider and healthcare organizations.

Bleeping Computer
AUGUST 24, 2023
Two vulnerabilities affecting some version of Jupiter X Core, a premium plugin for setting up WordPress and WooCommerce websites, allow hijacking accounts and uploading files without authentication. [.
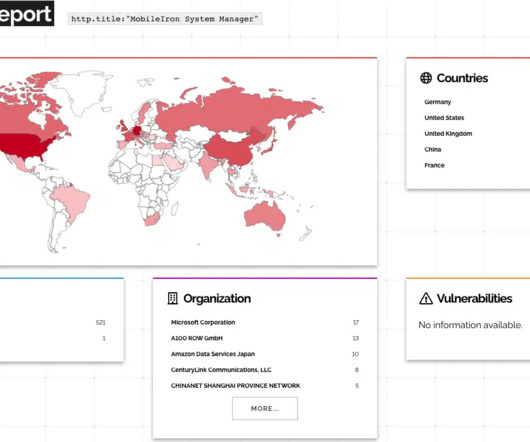
Security Affairs
AUGUST 24, 2023
Proof-of-concept exploit code for critical Ivanti Sentry authentication bypass flaw CVE-2023-38035 has been released. Researchers released a proof-of-concept (PoC) exploit code for critical Ivanti Sentry authentication bypass vulnerability CVE-2023-38035 (CVSS score 9.8). This week the software company Ivanti released urgent security patches to address the critical-severity vulnerability CVE-2023-38035 impacting the Ivanti Sentry (formerly MobileIron Sentry) product.

Bleeping Computer
AUGUST 24, 2023
Ransomware threat actors are spending less time on compromised networks before security solutions sound the alarm. In the first half of the year the hackers' median dwell time dropped to five days from nine in 2022 [.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.
Security Affairs
AUGUST 24, 2023
An 18-year-old member of the Lapsus$ gang has been convicted of having helped hack multiple high-profile companies. A teenage member of the Lapsus$ data extortion group, Arion Kurtaj (18), was convicted by a London jury of having hacked multiple high-profile companies, including Uber , Revolut , and blackmailed the developers of the gaming firm Rockstar Games.

The Hacker News
AUGUST 24, 2023
Public Wi-Fi, which has long since become the norm, poses threats to not only individual users but also businesses. With the rise of remote work, people can now work from virtually anywhere: a cafe close to home, a hotel in a different city, or even while waiting for a plane at the airport. Next, let's explore the risks of connecting to public Wi-Fi, both for you personally and for businesses.

Security Affairs
AUGUST 24, 2023
The FBI warned that patches for a critical Barracuda ESG flaw CVE-2023-2868 are “ineffective” and patched appliances are still being hacked. The Federal Bureau of Investigation warned that security patches for critical vulnerability CVE-2023-2868 in Barracuda Email Security Gateway (ESG) are “ineffective.” According to the feds, threat actors are still hacking the patched appliances in ongoing hacking campaigns.

WIRED Threat Level
AUGUST 24, 2023
Musician Alex Pall spoke with WIRED about his VC firm, the importance of raising cybersecurity awareness in a rapidly digitizing world, and his surprise that hackers know how to go hard.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Bleeping Computer
AUGUST 24, 2023
Cybercriminals behind the Smoke Loader botnet are using a new piece of malware called Whiffy Recon to triangulate the location of infected devices through WiFi scanning and Google's geolocation API. [.

Dark Reading
AUGUST 24, 2023
Embracing a risk-first mindset empowers organizations to make informed decisions, strengthen security, safeguard valuable assets, and reduce financial impact.

Bleeping Computer
AUGUST 24, 2023
The Federal Bureau of Investigation warned that patches for a critical Barracuda Email Security Gateway (ESG) remote command injection flaw are "ineffective," and patched appliances are still being compromised in ongoing attacks. [.
The Hacker News
AUGUST 24, 2023
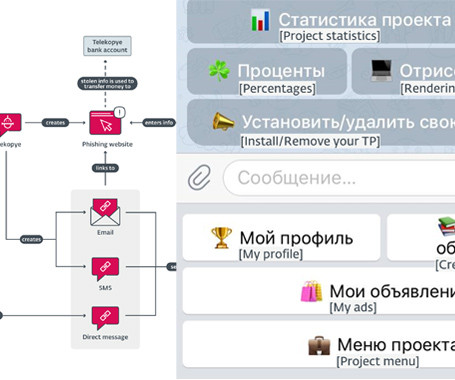
A new financially motivated operation is leveraging a malicious Telegram bot to help threat actors scam their victims. Dubbed Telekopye, a portmanteau of Telegram and kopye (meaning "spear" in Russian), the toolkit functions as an automated means to create a phishing web page from a premade template and send the URL to potential victims, codenamed Mammoths by the criminals.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

Malwarebytes
AUGUST 24, 2023
Today, I am absolutely thrilled to share some exciting news: Malwarebytes is officially welcoming Cyrus Security into our family. This acquisition signifies an exciting chapter in our journey, and I wanted to share why this development is so special, and what it means for the millions who trust Malwarebytes to keep them safe. We have always been committed to keeping you safe and secure in the digital landscape.

WIRED Threat Level
AUGUST 24, 2023
Russia tightly controls its information space—making it hard to get accurate information out of the country. But open source data provides some clues about the crash.

Heimadal Security
AUGUST 24, 2023
Hey there, fellow digital explorers! Welcome to a journey that promises to take your cybersecurity understanding to a whole new dimension. As the Stellar Strategist of Product Prowess (Head of Product Marketing) at Heimdal, I’m excited to guide you through the cosmic wonders of Heimdal XDR, an innovation that’s poised to transform the cybersecurity landscape. […] The post Into the Heimdalverse appeared first on Heimdal Security Blog.
The Hacker News
AUGUST 24, 2023
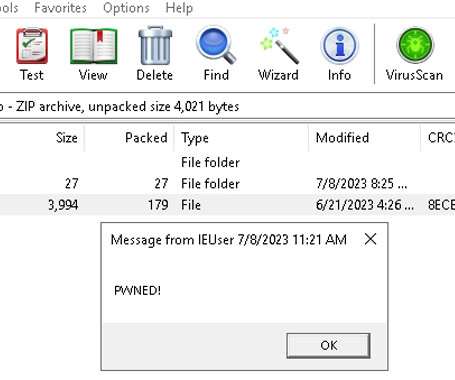
A recently patched security flaw in the popular WinRAR archiving software has been exploited as a zero-day since April 2023, new findings from Group-IB reveal. The vulnerability, cataloged as CVE-2023-38831, allows threat actors to spoof file extensions, thereby making it possible to launch malicious scripts contained within an archive that masquerades as seemingly innocuous image or text files.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Heimadal Security
AUGUST 24, 2023
The University of Minnesota is currently conducting an investigation into a substantial data breach that could potentially impact a large number of alumni and members of the university community. Millions Potentially Exposed The breach was brought to light last month when an unauthorized party claimed to have gained access to sensitive data stored within the […] The post University of Minnesota Reports Massive Data Breach appeared first on Heimdal Security Blog.
The Hacker News
AUGUST 24, 2023
The SmokeLoader malware is being used to deliver a new Wi-Fi scanning malware strain called Whiffy Recon on compromised Windows machines. "The new malware strain has only one operation.

SecureBlitz
AUGUST 24, 2023
What is the average cost of a laptop? Here is the answer. In today's world, computers have become an indispensable part of our everyday lives. They serve as invaluable tools for work, communication, entertainment, and so much more. However, when it comes to purchasing, the average cost of a laptop can vary greatly depending on […] The post What Is The Average Cost Of A Laptop?
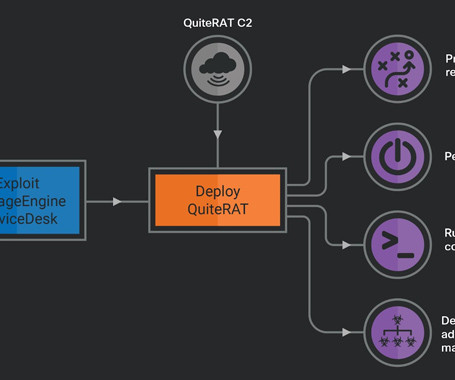
The Hacker News
AUGUST 24, 2023
The North Korea-linked threat actor known as Lazarus Group has been observed exploiting a now-patched critical security flaw impacting Zoho ManageEngine ServiceDesk Plus to distribute a remote access trojan called such as QuiteRAT. Targets include internet backbone infrastructure and healthcare entities in Europe and the U.S.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content