Weekly Update 357
Troy Hunt
JULY 20, 2023
Sad news to wake up to today. Kevin was a friend and as I say in this week's video, probably the most well-known identity in infosec ever, and for good reason. He made a difference, and I have fun memories with him 😊 Felt really sad waking up and seeing “RIP Kevin” in my timeline. I doubt there is a more well known name in our industry but if he’s unfamiliar to you (or you haven’t read this book), go and grab “Ghost in the Wires” which is an



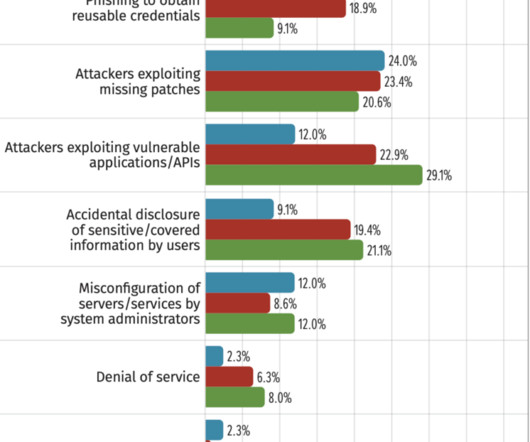



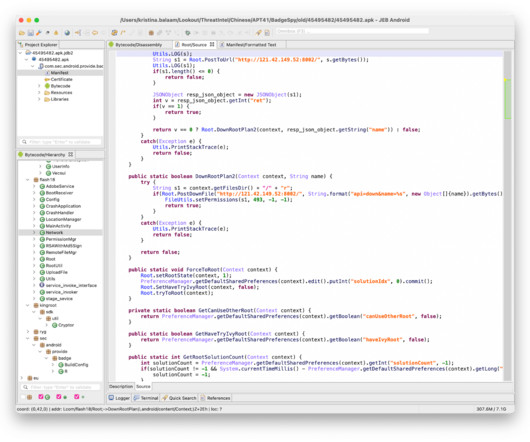

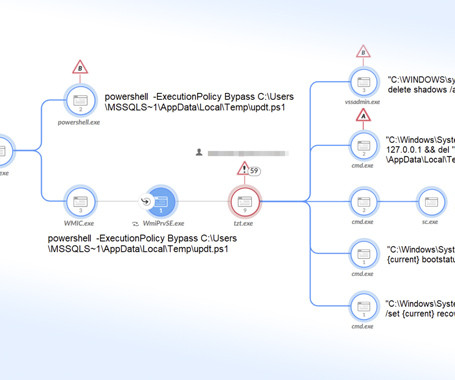































Let's personalize your content