Hacking Starlink
Schneier on Security
AUGUST 11, 2022
This is the first —of many, I assume—hack of Starlink. Leveraging a string of vulnerabilities, attackers can access the Starlink system and run custom code on the devices.

Schneier on Security
AUGUST 11, 2022
This is the first —of many, I assume—hack of Starlink. Leveraging a string of vulnerabilities, attackers can access the Starlink system and run custom code on the devices.

Krebs on Security
AUGUST 11, 2022
Image: Shutterstock. A cybersecurity firm says it has intercepted a large, unique stolen data set containing the names, addresses, email addresses, phone numbers, Social Security Numbers and dates of birth on nearly 23 million Americans. The firm’s analysis of the data suggests it corresponds to current and former customers of AT&T. The telecommunications giant stopped short of saying the data wasn’t theirs, but it maintains the records do not appear to have come from its systems
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
AUGUST 11, 2022
Google’s security guidelines also drew the majority of this year’s requests in apps, according to Kaspersky’s Privacy Checker website. The post 85% of Android users are concerned about privacy appeared first on TechRepublic.

Dark Reading
AUGUST 11, 2022
Industry standards would provide predictable and understandable IoT security frameworks.

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.

Tech Republic Security
AUGUST 11, 2022
Seeing your assets the way an attacker would look at them can help you spot where you’re exposed before you get attacked. The post Defend your network with Microsoft outside-in security services appeared first on TechRepublic.

CSO Magazine
AUGUST 11, 2022
In January 2018, the entire computer industry was put on alert by two new processor vulnerabilities dubbed Meltdown and Spectre that defeated the fundamental OS security boundaries separating kernel and user space memory. The flaws stemmed from a performance feature of modern CPUs known as speculative execution and mitigating them required one of the biggest patch coordination efforts in history, involving CPU makers, device manufacturers and operating system vendors.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Threatpost
AUGUST 11, 2022
Belgian researcher Lennert Wouters revealed at Black Hat how he mounted a successful fault injection attack on a user terminal for SpaceX’s satellite-based internet system.

SecureList
AUGUST 11, 2022
For more than a year, we have been providing free intelligence services via the OpenTIP portal. Using the web interface, anyone can upload and scan files with our antivirus engine, get a basic sandbox report, look up various network indicators (IP addresses, hosts, URLs). Later on, we presented an easy-to-use HTTPS-based programming interface, so that you could use the service in your own scripts and integrate it in existing workflow.
Dark Reading
AUGUST 11, 2022
Ransomware gang gained access to the company's VPN in May by convincing an employee to accept a multifactor authentication (MFA) push notification.

CSO Magazine
AUGUST 11, 2022
Predicting future technological performance is tricky business — we anticipate linear growth, but experience something different. So, as much as we might like to, we can’t predict the future by extrapolating from a straight line. Unfortunately for us forecasters, the dichotomy between expectation and reality makes it difficult to anticipate the exponential nature of technological progress , and that holds us back as change accelerates.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.
SecureBlitz
AUGUST 11, 2022
In this post, I will show you tips to share information using cloud storage secretly… Many people enjoy using Cloud. Read more. The post 6 Tips To Share Information Using Cloud Storage Secretly appeared first on SecureBlitz Cybersecurity.

CSO Magazine
AUGUST 11, 2022
Zero trust security management, extended detection and response ( XDR ), and a host of other threat and vulnerability management offerings were among the top products and services launched at Black Hat USA 2022 this week in Las Vegas. Black Hat is an annual global conference of security professionals, enthusiasts and vendors, serving as a stage for innovation in the cybersecurity field.
Security Affairs
AUGUST 11, 2022
Palo Alto Networks devices running the PAN-OS are abused to launch reflected amplification denial-of-service (DoS) attacks. Threat actors are exploiting a vulnerability, tracked as CVE-2022-0028 (CVSS score of 8.6), in Palo Alto Networks devices running the PAN-OS to launch reflected amplification denial-of-service (DoS) attacks. The vendor has learned that firewalls from multiple vendors are abused to conduct distributed denial-of-service (DDoS) attacks, but it did not disclose the name of the

Bleeping Computer
AUGUST 11, 2022
The U.S. State Department announced a $10 million reward today for information on five high-ranking Conti ransomware members, including showing the face of one of the members for the first time. [.].

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

eSecurity Planet
AUGUST 11, 2022
Many of the basic principles for securing a data lake will be familiar to anyone who has secured a cloud security storage container. Of course, since most commercial data lakes build off of existing cloud infrastructure, this should be the case. However, data lakes add additional elements such as data feeds, data analysis (data lake house, third-party analysis tools, etc.) which increase the complexity of interactions beyond a simple storage container.

Naked Security
AUGUST 11, 2022
Latest episode - listen now! (Or read the transcript if you prefer.).

CSO Magazine
AUGUST 11, 2022
Data breaches exposing consumers’ sensitive information continue unabated even as organizations amass and sell vast sets of consumers’ personal, financial, and location data to a thriving data broker industry. Concerns over the use of the growing stockpile of sensitive personal data have reached a fevered pitch in the wake of the Supreme Court’s decision to overturn Roe v.

Dark Reading
AUGUST 11, 2022
Even among businesses with cyber insurance, they lack coverage for basic costs of many cyberattacks, according to a BlackBerry survey.

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.

SecureBlitz
AUGUST 11, 2022
Here, I will show you ways manufacturers can benefit from going online… Some businesses are based entirely on the internet. Read more. The post Ways Manufacturers Can Benefit from Going Online appeared first on SecureBlitz Cybersecurity.

Bleeping Computer
AUGUST 11, 2022
The Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) warned US organizations today that attackers deploying Zeppelin ransomware might encrypt their files multiple times. [.].

CSO Magazine
AUGUST 11, 2022
Network misconfigurations cost companies an average of 9% of annual revenues, according to a study released Wednesday by a network security and compliance company. The research by Titania based on a survey of 160 senior cybersecurity decision makers across a broad array of government and industrial verticals also warned that misconfigurations that leave a business vulnerable to cyberattacks could be sitting on networks for months or years because of infrequent audits of connected devices.

Security Boulevard
AUGUST 11, 2022
Our cybersecurity predictions for 2022 predicted trends such as increased regulatory changes and exacerbated talent shortages. Several of these predictions have played out, but at just past the midpoint of the year, it’s worth delving into some cybersecurity predictions for the rest of 2022. Increased Attacks on OT With increased convergence between IT and operational technology (OT) systems, threat actors.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Bleeping Computer
AUGUST 11, 2022
Developers are furious at GitHub's upcoming privacy policy changes that would allow GitHub to place tracking cookies on some of its subdomains. The Microsoft subsidiary announced this month, it would be adding "non-essential cookies" on some marketing web pages starting in September, and offered a 30-day "comment period." [.].

We Live Security
AUGUST 11, 2022
A deep-dive in Zero-trust, to help you navigate in a zero-trust world and further secure your organization. The post An eighties classic – Zero Trust appeared first on WeLiveSecurity.

Tech Republic Security
AUGUST 11, 2022
The BlackBerry 2022 Threat Report is not a simple retrospective of the cyberattacks of 2021. It is a high-level look at issues affecting cybersecurity across the globe, both directly and indirectly. It covers elements of critical infrastructure exploitation, adversarial artificial intelligence (AI), initial access brokers (IABs), critical event management (CEM), extended detection and response (XDR), The post 2022 Threat Report appeared first on TechRepublic.

TrustArc
AUGUST 11, 2022
Why should you know where your data is? A centralized data inventory is critical for your organization’s security and privacy compliance and the starting point for understanding what and how data is collected and used across the organization.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.
Security Boulevard
AUGUST 11, 2022
Applying Identity to DevSecOps Processes. brooke.crothers. Thu, 08/11/2022 - 12:11. 5 views. Identity Means Secrets. You prove identity by validating credentials; secrets are the digital credentials used for that purpose. With the proper validation, you can authenticate a user (human or machine) and authorize them to access privileged services, accounts, and applications.
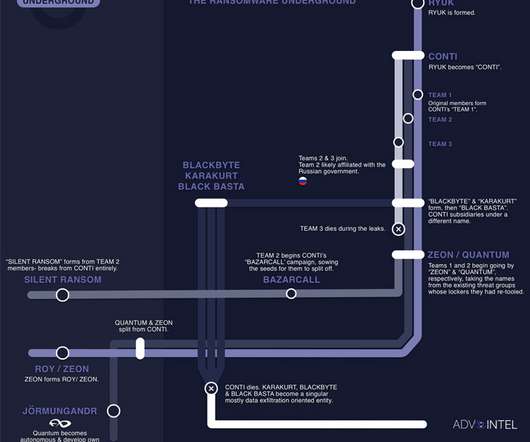
The Hacker News
AUGUST 11, 2022
Three different offshoots of the notorious Conti cybercrime cartel have resorted to the technique of call-back phishing as an initial access vector to breach targeted networks. "Three autonomous threat groups have since adopted and independently developed their own targeted phishing tactics derived from the call back phishing methodology," cybersecurity firm AdvIntel said in a Wednesday report.

Security Boulevard
AUGUST 11, 2022
MixMode’s unsupervised, third-wave AI computes patterns of interaction over many different timescales, contrasting it over the next 5-minute interval with what was seen previously. Should patterns deviate, the platform performs an assessment of the security risk implied in that deviation and presents it to the user. The post Understanding the Evolution and Impact of AI on Cybersecurity appeared first on Security Boulevard.

Tech Republic Security
AUGUST 11, 2022
While phishing remains the most common attack vector, threat actors have introduced tactics, techniques, and procedures that don’t require a victim to click on a malicious link or open a weaponized document to become infected. Instead, they are utilizing exploits, such as Eternal Blue, and uncommon programming languages and obscure data formats to deposit ransomware.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
Let's personalize your content